When your CIO sidles up to you and whispers sweet nothings that sound an awful lot like “Cybersecurity risk assessment,” those three little words are a sure sign that the honeymoon is over. But what isn’t dead is your spirit of optimism because in about six minutes you, dear reader, will know exactly how to perform a hecka good cybersecurity risk assessment.
So, sit back, gird your loins, and let’s get this step-by-grueling-step Cybersecurity Risk Assessment Guide on the road.
What’s A Cybersecurity Risk Assessment?
A cybersecurity risk assessment isn’t a fat report that punches a hole through your desk as it lands. A cybersecurity risk assessment is a living process – and a mighty fine one at that. It’s a process that:
- Identifies cyber threats to your business.
- Identifies weaknesses in your systems, protocols, and people.
- Analyzes and evaluates each risk revealed by those threats and weaknesses.
- Prioritizes those risks ready for mitigation.
OK, So What Do I Get Out Of A Cybersecurity Risk Assessment?
Your cybersecurity risk assessment is a beautiful framework for understanding cyber threats and their likely impacts, and how to prioritize them. Isn’t that enough? No? Ok, you also get:
- Credibility. Any business working toward a higher level of cybersecurity looks good to Big Fat Corps looking to do business. Stakeholders will trust you more, bless them.
- Compliance with regulatory beauties like SOC 2, HIPAA, etc.
- Optimized resources – you’ll spend your hard-won cybersecurity dollars on things that actually make a difference.
When (And How Often) Should I Do It?
It’s a process, sweetie. (Trust the process!) And that doesn’t mean this is a one-and-done situation, so we’ve listed some good reasons to kick the process off in the table below:
When To Perform A Cybersecurity Risk Assessment
| WHEN | WHY |
| Your business changes | Change brings with it new threats and vulnerabilities. Change can include new modes of working (e.g., remote working), buying new IT infrastructure, committing to compliance regulations, or entering new markets. A risk assessment helps you understand what the new risks are and how to minimize them. |
| You’ve been breached | Ouch! How did that happen? The horse may have bolted but a cybersecurity risk assessment will make sure that the horse never bolts again. It’ll also help gain your horsey reputation back. |
| Regulations change | Wait, what? You just achieved ISO 352524Q43 and they’ve changed Annex 4523523.34 to include that thing? Dangit, time to roll out the risk assessment. |
| As part of the continuous improvement cycle | That sweet, smug smell of a continuous improvement strategy should always address how you’ll continually improve cybersecurity. |
| As part of your IT strategy | An IT strategy articulates how IT supports business goals. Unless one of your business goals is to welcome basement hackers with open attack vectors, then risk assessments should be part of your IT strategy. |
Cybersecurity Risk Assessment: Your Step-by-Step Guide
Like any good process, your cybersecurity risk assessment has three phases and here they are:

Phase 1: Identify
Phase 1 is all about information-gathering. It’s about scoping out your IT ecosystem and what threatens it. Once you’ve got that down, you can assess how bad things are (but wait up, that’s Phase 2).
Phase 1 gets you to focus on identifying three things: your IT assets, their vulnerabilities, and the nature of the cyber threats likely to attack them.
It’s this kind of thing:
Cybersecurity Risk Assessment: Phase 1
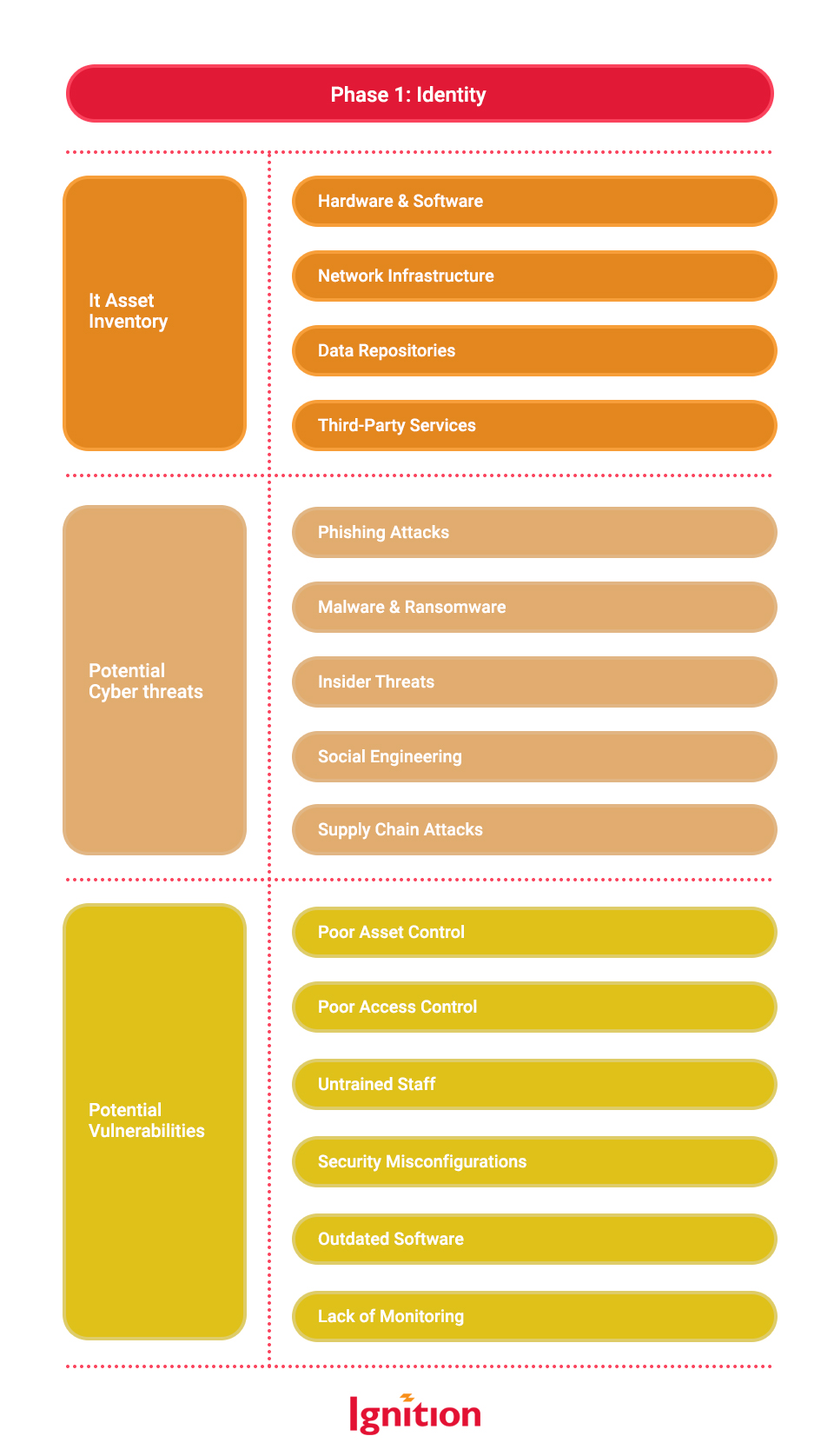
Identifying IT Assets
First off, make an inventory of your IT infrastructure – the IT that supports your business. This isn’t just the nuts and bolts of your devices and hardware, but takes into account your networking, the software, cloud services, and any third-party platforms you use – the whole IT enchilada. Identifying what you have and how you use it helps you work out what the risks are.
Identifying Potential Cyberthreats
Now you understand more about your IT infrastructure, make a list of the types of cyber threats that might be thrown at it. The usual suspects like phishing attacks, malware, and ransomware will top your list, but you’ll also want to consider stuff not aimed at you, but your connections, which brings supply chain attacks into the realm of possibility. If you’re proud of your toxic culture or you’re lax at hiring, go ahead and add insider threats to the mix.
Identifying Potential Vulnerabilities
Vulnerabilities are flaws or weaknesses in your IT ecosystem that could be exploited by a cyber attacker. Vulnerabilities aren’t just about misused software features, a software bug, or an ancient operating system. They’re people- and process-related, too, and include human error, impatience, frustration, and fear among the biggies.
Do any of these instances sound familiar? (Ahem.)
Your team regularly sidesteps authorized-but-useless apps in favor of unauthorized-but-useful ones? You’ve got no protocol or central control for forcing software updates? You may or may not have more than one set of backups? (Who knows?) Your CEO is so now-now-do-it-now that social engineering attacks work like a charm? These are some fine vulnerabilities right here. (You’re probably gonna want to draw straws to decide who tells the CEO they need to chill the flip out – but dialing back that kind of pressure can help reduce the company’s security risks.)
Phase 2: Analyze
You’ve identified your IT assets, their vulnerabilities, and those nasty threats waiting to jump-scare them. Now it’s time to assess the risk of each threat. In cybersecurity, risk is in a relationship with:
- The likelihood of a threat happening, which is usually expressed as a fraction.
- The impact of that threat, which indicates the resulting damage or consequences. It can be expressed in dollars, in downtime, or as reputational damage – whatever metric your brand values most.
It’s time to assign numbers to risk. The bigger the number, the bigger the risk – and the higher the priority to fix it. Wait up, that’s Phase 3. Let’s not get ahead of ourselves. Instead, let’s do some math. Here’s the risk formula:
Risk = Likelihood x Impact
Choose Your Criteria
| Examples of Likelihood Criteria | Examples of Impact Criteria |
| Historical Data Threat Intelligence Expert Opinion | Financial Loss Reputational Loss Operational Downtime Legal Consequences |
Let’s add some frosting to the bones, with a chilling example:
Forecast: Cold, Hard Truth From Real Human Experts
At HIP 2023, a global conference for corporate identity and access professionals, presenters offered chilling forecasts for increasing incidents of cybercrime:
- 80% of all breaches are linked to identity issues (e.g., ransomware, phishing, etc.)
- 75% of organizations will experience a breach in the next 12 months
- $4.35M = cost per breach (globally), or $9M in USD
- $2.5M = predicted average loss per breach
Historical data tells us that bad people will continue to do bad things. Thus, your people may well get snagged by the latest ransomware phishing scam (ahem, we got the numbers if you wanna play). And if they do, threat intelligence tells you that you’ll be locked out of your files for 48 hours for a serious operational loss. Nasty!
Sounds bad, especially with a better than 1-in-4 chance someone on your team could fall for the scam. So, does phishing go to the top of your “We gotta sort this now!” list? It depends. Maybe. Maybe not. You won’t know until you’ve assigned risk levels to each threat you’ve identified.
Phase 3: Prioritize
Some people think this is the easy part. Phase 2 has given you an assessment of the risk of each threat, so you should have a list of risk scores. Put the scores in bigness order (big at the top) and gee willikers! Now you have a list of risks in order of scariness and importance to your business. Use this list of priorities as a foundation for your awesome Plan of Action (feat. checklists) A.K.A, your Gap Remediation Plan.
Ahem. Risk isn’t just about evil cybercrime. For instance, if your goal is achieving CMMI compliance and something’s lacking, fixing it should be a high priority for you. The risk is that you don’t get compliance, and that means no big, juicy defense contracts for you – that’s a massive financial loss.
The final, less well-known phase of cybersecurity risk assessment is Phase 4: Sit Down And Cry It All Out, because if you’ve got through it all, you’ve done brilliantly. Gold star! (And tissues.)
Cybersecurity Risk Assessments Are Less Awful If You Get Some Help
Cybersecurity risk assessments aren’t one of the easiest or funnest business tasks, but they can be one of the most rewarding, financially, operationally, and peace-of-mindedly speaking. If you think it might be time to peek in the direction of risk reduction, we can do some cool stuff to make it easier – from a quick walk-through to point you in the direction of your worst vulnerabilities, all the way through to an all-you-can-eat gap remediation project that gets your risks mitigated like a decent boss. Call us. We’re here to help.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!

