Mobile device management (MDM) isn’t magic, but it’s the next best thing. It’s the tech solution to the ancient problem of monitoring and managing All The Devices, and all without having to get up off the sofa. It keeps all your gadgets in line – wherever they are in the world – from a centralized online platform.
So, how does MDM work? This wizardry isn’t born of pentagrams and incantations, but of a clever mechanism you may have heard of – the internet – plus an array of techie bits and bots that we’ll dive into in a mo. There’s also a heaping helping of human added to this joyous mix, because tech is not our overlord. Yet.
Before we get into how MDM works, why is it such a big deal? Here’s why:
Why MDM Is Such A Big Deal
It’s not just that MDM is clever and awesome in itself. The consequences of having a secured, monitored, and managed fleet of devices can give your business a truckload of advantages. Things like:
- A bigger talent pool. When you have the power to secure devices around the globe, you can hire from anywhere with confidence.
- A ton of data security compliance controls checked off the checklist. MDM’S built-in cybersecurity defenses and access control mechanisms means you’re well on your way to achieving shiny things like SOC 2 and HIPAA compliance.
- Flexibility, adaptability, and scalability for your specific business operations. Want to go fully remote? No problem. Want to hire at scale? Go ahead. Want to open up a kiosk-based side-hustle? Yep, no problem. MDM keeps remote devices safe and secure.
- Improved productivity. MDM’s device tracking, remote troubleshooting, and preventive maintenance keeps people online and productive, and unplanned downtime at a minimum. Your team has access to all the apps and files they need, without compromising data security.
- Cost savings. MDM keeps tabs on your devices – fewer replacements and better reserve device management means more dollars to spend on the fun things.
How Mobile Device Management Works
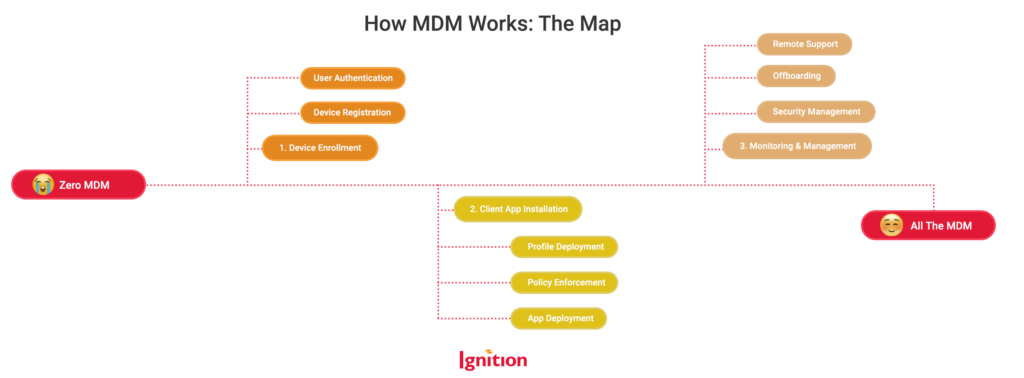
Let’s take you on an adventure from Zero MDM to All The MDM. Here’s the map:
How MDM Works: The Map:
Let’s make a start:
1. Device Enrollment
First off, it’s time to enroll those shiny devices into your awesome new MDM thingy. There are three ways to do it:
- Self-onboarding: Devices are enrolled manually by users following instructions. This is often used for Bring Your Own Device (BYOD) workplaces. In self-onboarding, your user will link the device to your MDM server via the internet.
- Admin enrollment: Devices are enrolled manually by an IT administrator. Admin enrollment is a prehistoric pain in the posterior for everyone, especially those IT admins stuck in the basement manually enrolling each device. Don’t do this.
- Automated onboarding: Automation uses zero-touch (corporate devices) or conditional access (BYOD) mechanisms. With zero-touch enrollment, devices enroll themselves, once they’re booted up and connected. Conditional access involves a little more user interaction, as they follow procedures to ensure their devices fall in line with corporate security policies – but we’re getting ahead of ourselves here.
Once devices are enrolled, best practices suggest employing User Authentication. To ensure users are actually who they say they are, you can use ID authentication methodologies like multi-factor authentication (MFA), tokens, or a biometric. These measures are built into the device/user enrollment process.
Finally, the MDM brain will gather information about devices via Device Registration. This process includes assigning unique identifiers, such as an individual Mobile Equipment Identity (IMEI) number and serial number, plus attributes like the make and model, operating system, and hardware specs. It’ll also link the device to the user. If you’re enrolling in bulk, you’ll see a magical IT asset inventory blossom before your very eyes.
2. Client App Installation
Installing a client app on the device allows the MDM server to communicate with the device and deploy the instructions coming in to land from the MDM server. This will include deploying:
- User and configuration profiles, which enforce a payload of settings, accounts, restrictions and credentials.
- Policy enforcements, which enforce security configurations.
- App management, which deploys role/seniority-based apps and access to the user’s device, and enforces a denylist to block unauthorized apps.
3. Monitoring and Management
This is where the fun really begins. With the device enrolled and all configured up, it’s time to monitor and manage that bad boy! With centralized control from a single dashboard, IT admins can run amok, monitoring the crap out of everything, depending on how hardcore they are. (Don’t panic: MDM allows for admin permission levels and a robust audit trail).
This means they can troubleshoot remotely if a user has a technical issue. They can offboard an employee remotely (and securely), by closing accounts and withdrawing permissions. They can manage security protocols, e.g., by enforcing software updates and MFA, or enforcing network access protocol – no unsafe airport wifi for you! And a whole lot more.
Your IT admin doesn’t have to sit at their MDM dashboard 24/7 to do all this. Much of the monitoring busywork is automated, including device compliance and security, OS update versioning, device health and network connections, as well as device location.
That’s How MDM Works. Good, Isn’t It?
Yes, we worship at the Church of MDM but that’s because MDM makes life so much easier for everyone. It’s a business asset for our clients and their people and, yep, we even use it ourselves. MDM looks so much more complex than it actually is – it just needs a little preparation, like deciding which role needs access to which apps, or whether to go rogue with BYOD. If you’re even a tad MDM-curious, give us a ring. We’ll talk your ear off about MDM til forever.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!
