Cyber security strategy is one of the most important aspects of business operations, as it can impact the company’s workflow, revenue, and brand reputation. Like any effective strategy, your cyber security strategy needs a plan of action, which is defined as a cyber security compliance framework.
But, before choosing a cyber security compliance framework to keep your business safe from cyber criminals, there are many factors to consider. And as your friendly cyber security professional, I can confidently tell you that the compliance framework you choose will significantly impact how well you are protected.
What Is a Cyber Security Compliance Framework?
Your business’s cyber security framework is a set of standards, policies, and practices developed to protect your data and IT systems.
Why Frameworks Are Worth the Effort
There are two main types of frameworks—mandatory and voluntary. Mandatory frameworks are issued by governments or regulatory agencies, while private sector organizations develop voluntary frameworks.
A mandatory compliance framework helps ensure you are compliant with the law. These frameworks also help you stay ahead of regulation changes while simplifying the process of maintaining compliance over time.
Having a framework in place will help you sleep more peacefully at night, knowing that your business is operating ethically and legally.
Let's take a look at these alarming cyber attack threat statistics from the last couple of years:
- According to RiskIQ research, cyber crime costs organizations $2.9 million every minute.
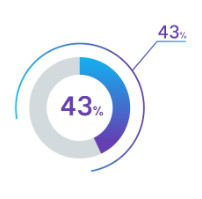
- In 2019, over 43% of data breach victims were small businesses.
- The U.S. holds a trophy of shame for having the world’s highest data breach costs, with average attacks costing $8.6 million, according to IBM’s Cost of a Data Breach report.
You need a team of experts and a clear framework driving your data security. Your framework needs to be tailored to your needs and should also depend on the sensitivity of the data you’re storing. The more sensitive the data you’re storing, the more vulnerabilities you have. Which means you’ll need more robust security.
Although it may seem difficult at first, once you have a plan in place, it’s so much easier to manage your company’s risks since your team will know exactly what your protocols are. A security strategy is only effective if it’s followed consistently.
Here’s a simple recap: frameworks are worth the effort because: 1) they offer protection against the latest cyber attacks 2) they help you stay compliant with regulations and avoid fines.
Thank you for coming to my Ted Talk.
The Top 5 Cyber Security Compliance Frameworks and Their Purposes
There are many different compliance frameworks you can choose from, so it’s crucial to find a framework that suits your needs best. Fortunately, I’ve created this list of the most popular frameworks and their primary purposes to make that easier for you:
1. NIST Cyber Security Framework
The cyber security framework from the National Institute of Standards and Technology is a voluntary framework that provides a cyber security strategy, with control objectives (which define the risk categories for a process or sub-process), for managing cyber security within an organization. This framework provides a standard way to think about cyber security and its relation to your business operations. This framework consists of four essential elements:
- Identify
- Protect
- Detect
- Respond
2. ISO 27001 and ISO 27002
ISO 27001 is an internationally recognized standard used to guide organizations through implementing, maintaining, and improving their information security management system or ISMS—which is a set of security controls that protects the confidentiality and integrity of assets from threats. An ISO 27001 certified organization should ensure that they manage the risks associated with information security, protect information assets, and align security controls with their business objectives.
The ISO 27002 framework is a set of guidelines that provides your organization with standard practices for managing your cyber security risks. The ISO 27002 framework recommends that your organization have a documented strategy for identifying the threats to your systems. You should also have a documented strategy for mitigating those threats by developing appropriate controls for your particular needs.
3. SOC 2
SOC 2 is an internationally recognized cyber security framework—with greater focus and preference in North America—that helps protect data privacy, integrity, and availability. It consists of various standards to ensure that your organization follows accepted practices in the industry.
The purpose of SOC 2 is to help organizations maintain compliance with the ISO/IEC 27001 standard for information security management systems. SOC 2 also provides guidelines on meeting the standards set forth by US law for information security management systems, specifically Section 508 of the Rehabilitation Act of 1973 and Section 1175(g) of the Social Security Act.
4. HIPAA
HIPAA, or the Health Insurance Portability and Accountability Act of 1996, is an excellent example of a compliance framework that many enterprises are required to abide by to protect the confidentiality and integrity of their patient's medical information.
This framework was created in 1996 in response to growing concerns about the integrity of healthcare data. HIPAA regulations are remarkably strict concerning the handling of confidential data, especially when it comes to electronic communications. Mis-delivered emails or letters can be construed as violations of this act.
5. GDPR
The General Data Protection Regulation or GDPR is EU-wide legislation that was created to harmonize data privacy laws across the entire union. It imposes strict conditions on the use of personal data and sets out rules for processing this data. The GDPR contains explicit requirements for compliance issues, data breach notification, and data protection impact assessments.
The EU's General Data Protection Regulation covers these main principles:
- Personal Data must be processed lawfully, fairly, and transparently.
- Data subjects must give their consent before processing their personal data for any purpose other than the purpose it was collected for (known as “purpose limitation”).
- Personal data may only be processed when necessary to.
Stop Waiting and Start Securing Your Organization
It is always better to control your cyber security environment rather than be reactive to an incident. With new threats coming up every day, it's essential to stay updated on the latest cyber security frameworks and compliance standards. And the friendly, cyber security experts at Ignition are here to help.
We offer the latest protection to keep your data, sensitive information, and network safe. Ignition protects your business so you can focus on what's important—growing your business. We offer a comprehensive cyber security solution, and the peace of mind that comes with a robust cyber security framework.
Still, have questions about cyber security compliance frameworks or how to get started? Give us a call. We’re here to help!
