How do you manage your employees’ personally-owned devices? Re-brand the annual technology distribution chore and evoke a party! Dump the purchase orders and introduce a company-wide bring your own device (BYOD) policy to tap the unplumbed depths of gadget-love and employees’ familiarity with their own devices.
Establishing a BYOD policy may even be more effective than corporate-supplied devices — reducing costs while boosting employee satisfaction. Most places employ a mixture of folks, including those who safeguard vintage tech like it’s an Emotional Support Device and the techno-savvy digerati who swap out their gadgets every quarter, or as soon as they’re bored — whichever comes first.
So, let’s face it: convincing a diverse crowd to part with personal mobile devices, tablets, or laptops in exchange for corporate equipment could easily require expert-level negotiation skills. And in these cases, a BYOD policy could be the perfect solution.
In recent years, bring your own device (BYOD) policies have become more popular in the workplace for a number of valid reasons. When paired with the right support and security protocols, companies can enjoy the benefits of lower IT costs and possibly reduce their corporate carbon footprint.
What Is BYOD?
BYOD policies are corporate agreements that empower employees to use personal devices like mobile phones, tablets, laptops, or desktop computers to complete work-related tasks. While many corporate-owned business-only (COBO) policies still distribute tech tools with limited capabilities, the BYOD policy emerged over the last decade as a disruptive innovation that has completely changed how employees interact with workplaces.
From accessing company emails and software applications to connecting securely with corporate networks, BYOD fosters a flexible, efficient work environment tailored to the individual. This rosy hypothetical comes with hidden thorns, however metaphorical. For example, suppose your company plans to initiate a bring your own device policy to increase employee productivity and save costs — two frequent outcomes. In this case, brand leaders must also consider how BYOD could open up gaps in security.

A company with no control over personal devices with access to sensitive information faces significant risks from hackers, ransomware, and other social engineers who prey on subpar security measures. Just like the gamble of eating potato salad at a potluck dinner, companies take chances with employee-owned devices they can only hope are “clean,” or free of viruses and other infectious malware (like food poisoning from potato salad that’s been out too long).
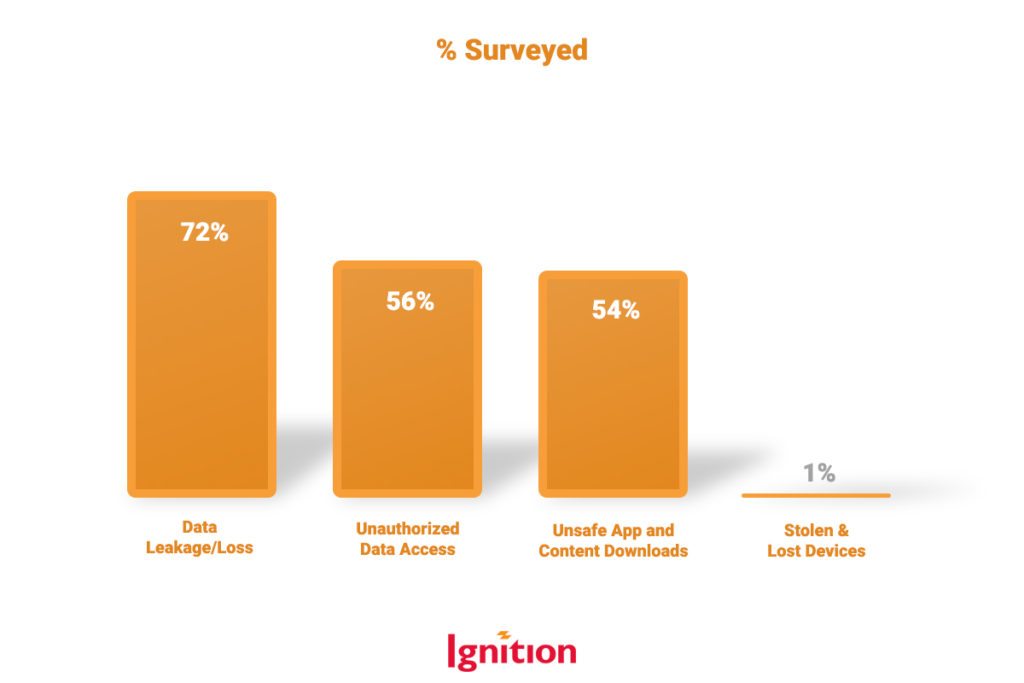
To highlight the reality of such threats, a recent Crowd Research security study on BYOD found data leakage/loss as the top security concern for 72% of companies surveyed. Another 56% reported concerns about unauthorized data access, and 54% worried about employees downloading unsafe apps and content. Stolen and lost devices ranked as known issues, but pose reduced security threats.
Benefits and Drawbacks
A preview of BYOD policy pros and cons is like a cheat code for navigating the complex clickstream of workplace technology. Below, we’ll explore some BYOD nuances and highlight potential benefits, drawbacks, and security concerns that demand proactive solutions.
| BYOD Policies: Benefits vs. Drawbacks | |
| Benefits | Drawbacks |
| More productive employees | Data security concerns |
| Cost-effectiveness | Complex IT support |
| Flexibility | Compatibility issues |
| Sustainability | |
| Relevance | |
Benefits of BYOD
Let’s start by reviewing the positives of BYOD policies before addressing any negatives that might curb your initial enthusiasm, such as:
- More productive employees. Happy meats are productive meats. Allowing employees to use their favorite tech tools for greater job satisfaction and productivity is like responsive design for your company’s virtual workplace.
- Cost-effectiveness. Abandon your cart and reduce IT spending; allocate resources wisely for a more financially savvy approach.
- Flexibility. People who use their own devices for work can easily switch between work and personal tasks. Remember when the lines between work and personal tasks were more clearly drawn — on the dead-tree version the employee handbook? Nobody wants to relive that.
- Sustainability. BYOD policies create opportunities to reduce corporate needs for additional tech devices and can be tweaked to incentivize employees to trade in and recycle their personal machines.
- Relevance. Stay ahead of business trends with BYOD to attract new talent who prefer to use their personal devices at work. Like growth hacking for HR, adopting this popular policy showcases your brand’s adaptability and commitment to remaining competitive.
Drawbacks of BYOD
Now that you’re ready to swipe right on BYOD, let’s look at some places where the glitter’s worn off. Some potential challenges will require a strategic policy approach to resolve, including:
- Data security concerns. BYOD’s lack of control over devices with access to sensitive information poses greater risks of unauthorized access and data breaches.
- Complex IT Support. When building your bring your own device policy, you’ll need to evaluate increased security risks to decide whether to implement continuous device and network monitoring. Managing different hardware and operating systems will make IT support more challenging.
- Compatibility issues. Different devices, operating systems, and applications all need different dongles, and can lead to compatibility issues.
Security Considerations and Solutions
If acknowledging the potential risks didn’t trigger a sudden biobreak and you’re still reading, we’d like to emphasize how the convenience of highly coveted BYOD policies can help level-up employee productivity and satisfaction. Despite potential (but manageable) security threats, allowing employees to use personal devices to access company platforms and resources remotely is a sensible business decision.
However, addressing malware and other risks that could jeopardize company networks is critical for success — especially in a BYOD environment with shaky perimeters and multiple devices with access to sensitive information. Brand leaders must also prepare contingencies in response to unauthorized access and lost or stolen employee devices — and maybe put an upper limit on the number of laptop replacements.
Organizations must prepare for scenarios in which compromised devices put company data at risk to unauthorized viewers. When employees leave their jobs, managers will need to limit network access and rely on procedures that ensure de-provisioning and data-wiping of all personal devices. Any access points that remain open on personal devices turn into hacker-bait that can threaten the company’s data security.
We’ve listed several security considerations and solutions below to get you started.
1. Mobile Device Management (MDM)
Organizations that embrace BYOD policies to boost workplace productivity and flexibility should implement a robust MDM strategy. MDM empowers IT administrators to effectively secure, control, and enforce security policies across a wide array of endpoints, from mobile devices to laptops and computers. Leveraging MDM can ensure the implementation of solid security configurations, remote data-wiping capabilities, and even device-tracking in case of loss or theft.
MDM’s significance extends beyond a mere security solution for mobile work environments; it also encompasses essential processes, policies, and human decision-making. This holistic approach creates a cohesive and secure mobile work ecosystem that maximizes efficiency while minimizing risks.
2. Security Training and Awareness
Prevention is key in cybersecurity. Provide training to educate employees about phishing threats, malware, and safe data handling processes. Build a company culture that values safety and helps employees better understand their roles in protecting sensitive data.
3. Policy Formulation
Your company policies should cover security guidelines, acceptable device usage, and consequences for non-compliance. Make sure to prioritize comprehensive device management and strict authentication protocols to fortify security defenses.
Policy Guidelines
Once your workforce is on board with building a Bring Your Own Device Policy, you will need to craft clear, well-defined guidelines. If you’re not sure where to start with policy guidelines, this section provides a concise overview for successful BYOD implementation.
These essentials (while not exhaustive) can help you create a secure and productive workplace that also fosters open communication.
1. Device Eligibility and Security Requirements
Your BYOD policies should define device eligibility and specify security standards, including antivirus updates, encryption protocols, and authentication measures.
2. Acceptable Use Policy
Outline company expectations for acceptable device use during work hours and while accessing company resources. Define prohibited activities to mitigate security risks.
3. Data Privacy and Handling
Establish guidelines for handling company data on employee devices that emphasize privacy and confidentiality. Implement secure data storage, backup, and decommissioning procedures to minimize data breaches.
Ignition—Building a Bring Your Own Device Policy Success
At Ignition, we are way more than just a team—we are Silicon Valley’s foremost experts in IT security, compliance, and support. We know building a Bring Your Own Device policy can be a challenging process when it’s DIY. But when you partner with Ignition, you’ll benefit from our comprehensive suite of services, including Mobile Device Management, Cross-Platform Support, Patch Management, A.I.-Driven Anti-Malware, Fleet Encryption, and much more, ensuring your company’s journey toward a productive BYOD environment is seamless and secure!
Don’t hesitate to reach out and jumpstart your BYOD implementation. Contact us now to explore how we can team up and make IT support and cybersecurity solutions your ultimate competitive advantage!
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!
