Does your to-do list look like this?:
- Improve reputation with customers
- Feel confident about data security
- Reduce the risk of data breaches
- Get dog food
- Make business processes more streamlined
If so, here’s how to do all that in one go. It’s time to dip your toes into the crazy world of SOC 2. SOC 2 is a data security and privacy accreditation that checks all the boxes (except the dog food), and it’s an almost must-have if you’re dealing with customer data. So, here’s a fast and furious look at the SOC 2 certification process.
Hang On, What’s SOC 2, And Do I Have To Do It?
SOC 2 is short for the oh-so-memorably-named Service Organization Control 2 and was created by accountants (yes, accountants, whom we love dearly). The American Institute of Public Service Accountants (AICPA) created SOC 2 way back in 2010 as a way to standardize and assess how well (or not) organizations looked after the security and privacy of customer data.
SOC 2 isn’t compulsory. No law says you gotta do it. But it’s a way of demonstrating that you’re committed to data security and privacy for your customers, and it’s becoming expected. And if you’re a startup, SOC 2 makes you look like a restaurant with a Michelin star. Just as a Michelin star recognizes a restaurant’s excellence in food quality and service, SOC 2 compliance is a respected standard that recognizes excellence in data privacy and security. That way, investors can be confident you won’t blow their investment on legal fees after your customer data goes public (or back to the restaurant metaphor, you’re worth the hype).
Ready to Get Your SOC 2 On? Let’s Talk About What It Really Means
SOC 2 has a set of criteria for you to meet. These criteria are chunked up into five categories called “trust service categories,” each of which requires particular controls. Let’s break those bad boys down in a table:
| The Five SOC 2 Trust Service Categories | |
| Security | Protection from unauthorized access and use, modification, or destruction of data or systems. |
| Availability | Ensures data or systems are available for use as agreed with or expected by your customers. |
| Confidentiality | Similar to the “Security” category — protects data and systems from unauthorized access, use, etc. |
| Integrity | Ensures that data is processed correctly: authorized, promptly, accurately, and completely. |
| Privacy | Ensures data is treated as per privacy laws: this includes collection, use, modification, and disposal of the data. |
The SOC 2 Certification Process: Where Do You Even Start?
The good thing about the process is that you’re not the first to tackle it. There’s a whole industry behind gaining SOC 2 accreditation, and there’s a tried-tested-trusted methodology that you’ll apply to your own business. This is what it looks like, roughly:
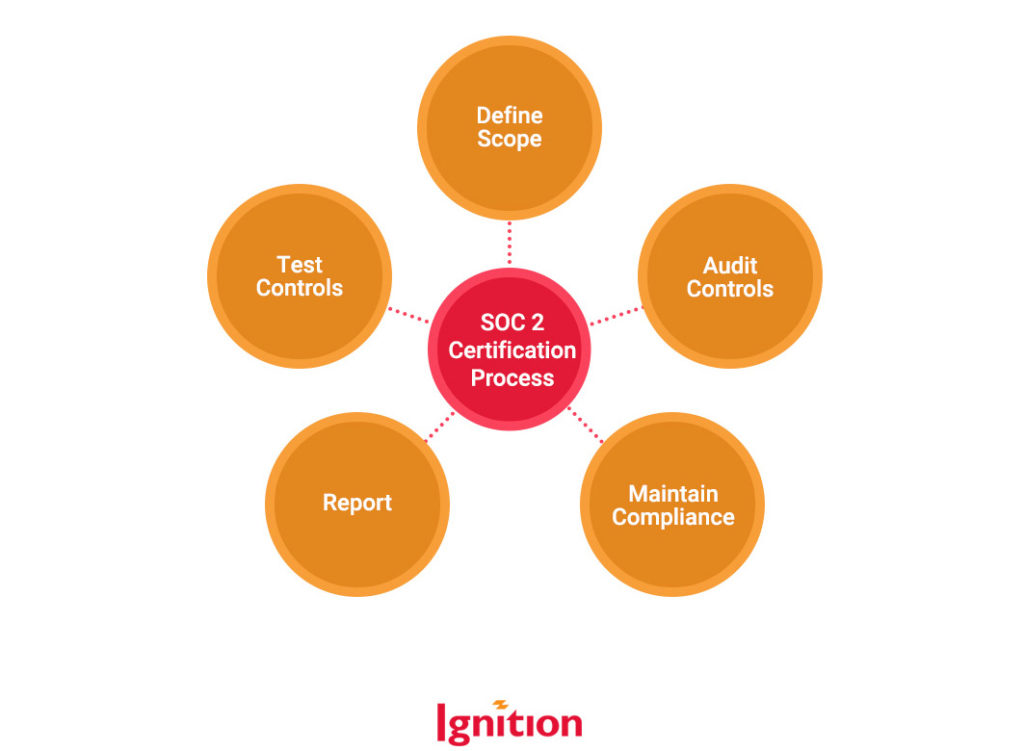
You’ll be busy defining your scope and maintaining compliance, while your SOC 2 auditor will be auditing, testing, and reporting like a pro. Because they are the pro, and you’re not.
Step 1: Define Scope
Here’s where you’ll decide what in your business is relevant to SOC 2. What customer data do you use? What systems do you use? How do you use the data? Not every aspect of your business will be relevant to SOC 2, and only the “Security” trust service category is mandatory.
Step 2: Audit Controls
Behold, your independent and qualified SOC 2 auditor strides about your business, taking a long, hard look at the security controls you have hurriedly put together to protect that sacred data. They might be looking for the existence of things like:
- All the encryption that ever was.
- Properly configured MDM.
- An IT asset register that’s actually up to date.
- Remote lock & wipe facility for your mobile fleet.
- DNS filtering.
..and more.
Step 3: Test Controls
Once your auditor has listed the controls you have in place, it’s time to test them out. They’ll do this by talking to your people and observing them in action, reviewing your data security policies, and trying to bust through your controls, e.g., to get unauthorized access to some of that sweet, sweet data; or maybe testing how you process your data to check for completeness.
Step 4: Report
Here’s where your auditor sits down with a tall beer, writes up their findings, and hands you over their report. There are two types of report, and you’ll have agreed with your auditor beforehand which report they’ll prepare for you:
| SOC 2 Audit Report | What it covers |
| Type 1 | This reports on your controls at a snapshot in time, e.g., yesterday |
| Type 2 | This reports on your controls over a period, e.g., over six months |
I Have My SOC 2 Report, And Now I’m Depressed
No, no, no. You should be setting fire to beacons because now you know how to get fully SOC 2 compliant. You’ve been handed a list of checkmarks and gaps, which are your path to glory because when you’ve finished remediating them (fixing them), you’ll be SOC 2 compliant.
Your first step is putting together a gap remediation plan. Its elements look something like this:
| SOC 2 Gap Remediation Plan Elements | ||
| What it is | What it does | Example |
| Nature of gap | Describes the gap to be remediated | Cripes! The OS on fleet devices hasn’t been updated for months |
| Cause of gap | Identifies why this gap happened/keeps happening | Automatic updates not switched to “on”/ Users can bypass update messages |
| Risk of gap | Assess the likelihood of bad stuff happening and the consequences if it goes unresolved. This helps you put your gap fixes in priority order. | Hackers can attack known vulnerabilities in outdated software: risk is high, so let’s prioritize this. |
| Action to take | Notes on how you will fix this gap, who’s responsible for fixing it, the timeline, who’ll be monitoring the fix, etc. | Joe will configure MDM to enforce automatic updates by Tuesday. Samir will amend the acceptable use policy to specify employees must accept updates by the end of the month. Neela will monitor the fix. |
Gap Remediation Is A Thing, And We Do It
If you’re not sure how your IT infrastructure can stand up to the SOC 2 certification process, then that’s perfectly normal. It can seem overwhelming, and not every, or even any, organization gets it right the first time. SOC 2 accreditation is an effort, taking resources and time, but the benefits of accreditation are cool, and you’ll never be starting from scratch. For instance, our style of MDM checks off 28 SOC 2 controls alone. If you’re thinking of SOC 2, or have just been handed a report the size of a bus by a laughing SOC 2 auditor, call us because we can help you fix (remediate) those gaps quickly.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!

