“I love clicking all the fire hydrants in this CAPTCHA thing,” said nobody ever, which is why the tech overlords invented two-factor authentication. All CAPTCHA does is separate the bots from the people. Two-factor authentication gets you to prove that you are, in fact, you. Is it awesome? Yes, it is. Does it have a few downsides? Sadly, yes. So let’s grab an Egg McWhatsit and take a cholesterol-lowering dive into the pros and cons of two-factor authentication, plus sniff out some good practices (and breakfast), just for good measure.
Remind Me, What Actually Is Two Factor Authentication?
Two-factor authentication (2FA) is an important component of identity management. Its purpose is to verify the claimed identity of an individual by requiring two (or more) different types of identity credentials. If you can’t prove you’re you, 2FA will do one of three things:
- Prompt a retry
- Ask for another type of credential
- Temporarily lock you out of those files you desperately need, like, right now.
Rather than being a pain in the glutes, 2FA is an effective and fairly straightforward way of lassoing data or files with another layer of security.
What Are The Principles of 2FA?
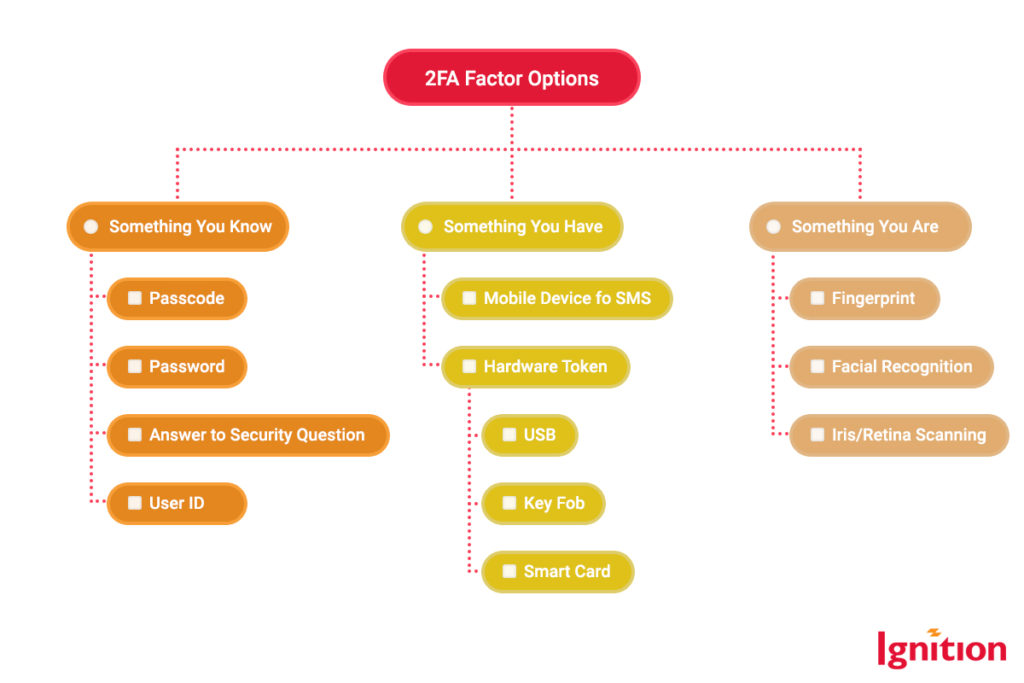
2FA requires you to prove that you’re using a combination of factors only you can provide. It’s looking for:
- Something you know: a passcode, password, user number, or memorable word.
- Something you have: a smartphone to which a verification code is sent.
- Something you are: a biometric, such as your fingerprint as Touch ID on a Macbook.
2FA is pretty much a security standard across many organizations and platforms and is also a requirement of compliance frameworks such as PCI-DISS. As a yes-we-do-this-now thing, developers have evolved a range of different second/third/fourth factors that look something like this:
The Pros And Cons of Two-Factor Authentication
Here’s the thing. 2FA is overwhelmingly a good thing because it works. But there are a few downsides, given that humans are involved. Here’s our take:
| Pros and Cons of 2FA | |
| Pros | Cons |
| Enhanced security: Two or three extra security requirements add extra levels of security. | User perception: Extra level of authentication may frustrate some users. |
| Reduces risk: Even if password attacks succeed or the smartphone is stolen, the hacker still needs another factor to break into the system. | Dependence on a second factor: E.g., if a smartphone is misplaced, the user will be blocked from their account. |
| Flexibility: IT leads can choose which second factors to deploy. | Resistance to change: If users are unfamiliar with 2FA, it could feel intrusive. |
| Compliant: 2FA is a standard requirement or recommendation for security frameworks like SOC 2. | Integration complexities: Integration of 2FA takes time and resources. |
Best Practices for 2FA
Throwing all the 2FA at all your people doesn’t always make for a great user experience. And, yes, data needs to be secure, but with some best-practice 2FA deployment, you can have all the security and a happy, unfrustrated workforce. Here are our top four tips:
1. Don’t Forget About Strong Passwords
2FA doesn’t mean the extinction of strong passwords. 2FA is an “as well as” rather than an “instead of.” Encourage your people to use a password manager to create and store complex passwords.
2. 2FA The Heck Out Of All Your Accounts
It’s good practice to use 2FA on all your accounts that support it and hold sensitive data. Think, “What do I need to protect?” and protect it.
3. Use More Secure Factors
SMS codes have the potential to be hacked, intercepted, or spoofed, so deploy hardware tokens or app-based authenticators, which are free and widely available, e.g., from Google, Microsoft, LastPass, or Authy, and provide time-restricted access codes.
4. Backup and Store Recovery Codes Securely
When you set up 2FA, don’t forget to back up your recovery codes in an encrypted file or password manager. Hopefully, backing up your 2FA codes will be an integral part of your cool backup strategy.
Two-Factor Authentication The Easy Way
Gotcha! Nothing’s easy in data security. But it doesn’t have to be difficult, either. 2FA is a widely accepted data security protocol, and you’ll already use it in your personal life for online banking, etc. But it’s good for your business, too, and accepted by consumers of B2C organizations, so it’s worth making sure you’re using it to your full potential. FYI, our 2FA expert would love to shoot the pros and cons of two-factor authentication and how to deploy it perfectly in your business. Give them a call now.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!
