Everyone loves a good policy because good policies make good things happen. And when your awesome fleet of mobile devices is all dressed up with the right mobile device security policies, you can unclench those glutes. You’ll know your data is safe, your clients can trust you with their stuff, and your people can work effectively and hacker-free.
So let’s take a quick streak through mobile device security policy and what you should probably know about. Warning: there are a LOT, so brace yourselves and keep your arms and legs in the vehicle at all times.
Policies Schmolicies. They Ain’t Worth A Dang.
You’re wrong, buddy. You got a good mobile device security policy (more than one, ideally), and you got:
- A headstart with all the compliance: SOC 2, HIPAA, PCS-DISS, and even that foreign stuff GDPR all need tight security policies.
- Data protection in all the right places: Data breaches are expensive in terms of downtime and reputation.
- Effective workflows and bigger talent pools: When you’ve got safe remote working down, you can hire from anywhere, go hybrid or fully remote.
- A plan if things go wrong: Got problems? Good policies will help your people know how to report it and how you go about fixing it.
We’ve chunked up our favorite best practice policies into semi-useful groups because it’s a lot to unpack.
Group 1: Management Policies
Check this out:
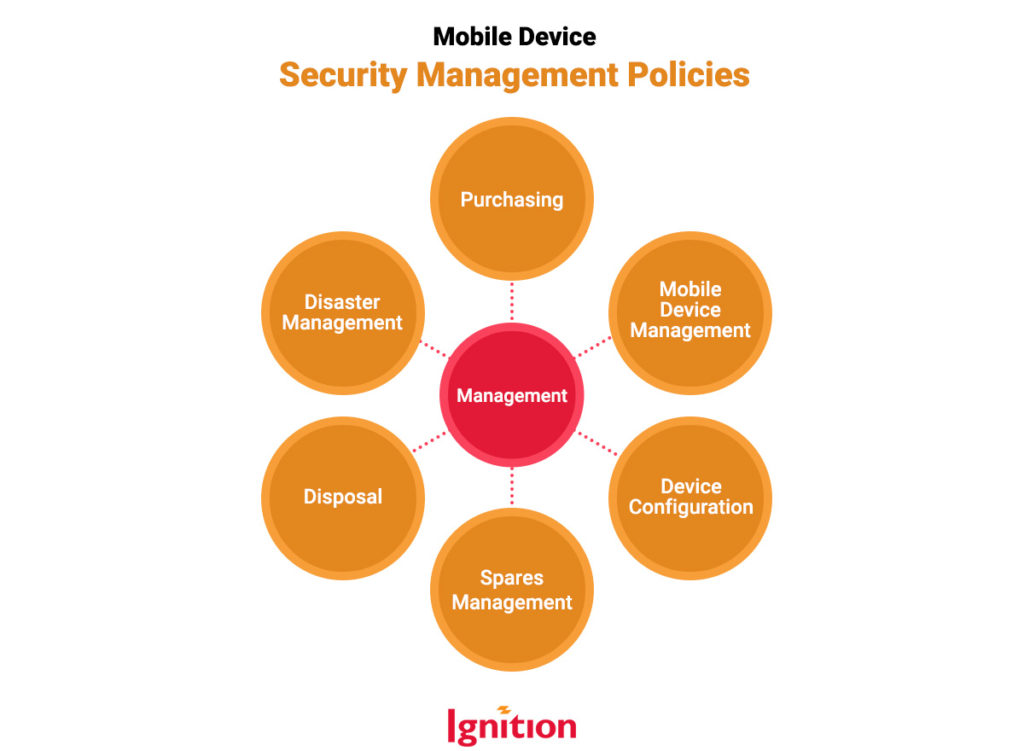
These policies set out how you’ve chosen to manage security, and the aspects of security to consider at each lifecycle stage of your mobile assets, e.g., laptops, tablets, smartphones, etc.
| Management Policies | |
| Policy | What it covers |
| Mobile Device Management | Requires that all devices in your fleet be managed centrally through MDM and comply with corporate security requirements. Includes the requirement for an IT asset inventory, updates, device encryption, backups, and other device security configurations |
| Purchasing | Requires need for vetting suppliers and devices for security, the levels of security, e.g., antivirus software is expected. Requires changing supplier passwords in new software. |
| Device Configuration | This governs the scope and standards of how each device in the fleet should be configured for security. You’re looking at security protocols such as device encryption, antivirus software, automatic updates, whitelisting, authorized apps, and insecure wifi blocking. |
| Spares Management | Requires spares to be maintained, checked, and physically protected. |
| Disposal | Requires devices to be wiped of data and disposed of responsibly. |
| Disaster Management and Incident Recovery | Outline your plans and roles when really bad things happen. |
Group 2: Access Control Policies
Controlling access is all about ensuring that only authorized people can access data or systems. Unauthorized people aren’t just hackers — they might be people in your organization. For instance, your salespeople shouldn’t have access to your HR records. And access is all about permission levels, too.

These policies set out your requirements about who can access data and how they do it.
| Access Control Policies | |
| Policy | What it covers |
| Principle of Least Privilege | This restricts access to data or systems only to those who need it for their roles. This includes role-based provisioning and cloud access, role-based permissions, and network segmentation. |
| User ID Management | Before access is authorized, users must prove their identity. This might be done through identity and access management tools such as multi-factor authentication and cloud single sign-on. Onboarding security protocols such as zero-touch onboarding will also verify users and prompt account closure when people are offboarded, securing any former employee access points. |
| Passwords | Strong password policies articulate how people should use and manage their passwords. Devices should be required to have a PIN or complex password to unlock them, which is frequently changed, perhaps through enforced updates. |
| Physical Security | Physical security policies may require device tracking to track missing devices and remote lock and wipe. Users may be required to lock and keep their devices safe. |
Group 3: People Policies
Data security depends greatly on the behaviors and attitudes of your humans happily tippy-tapping their keyboards. That’s why your mobile device security policies should always contain people-related stuff, like this:
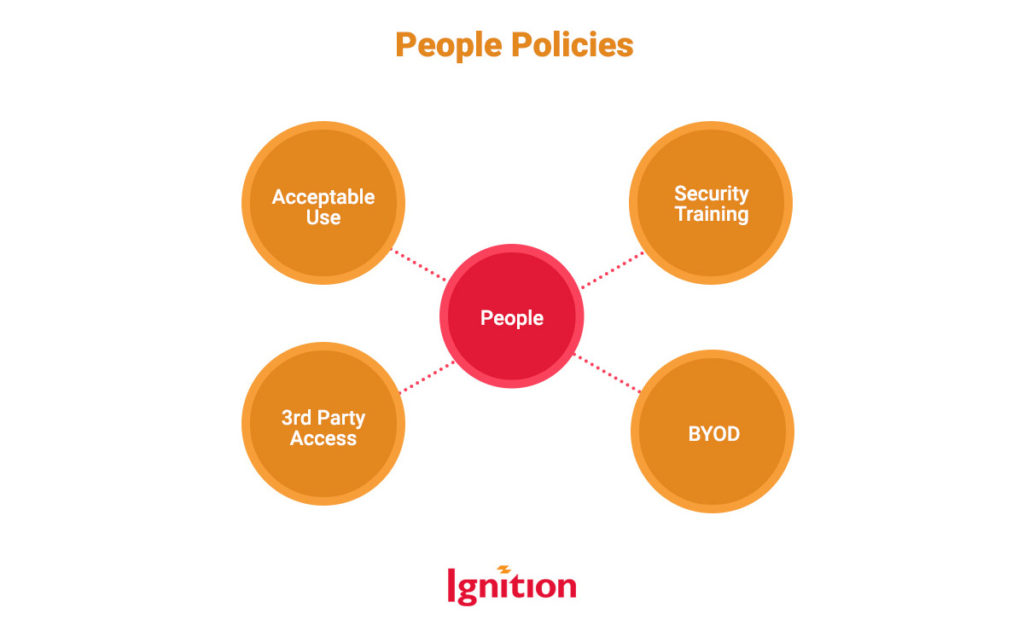
These policies contain guidance, requirements, and expectations that help your people stay unhacked, unbreached and un-phished.
| People Policies | |
| Policy | What it covers |
| Acceptable Use | An acceptable use policy guides your people on how they can use their device — and how they can’t. For instance, can they use their corporate device for personal use? What apps are authorized? Do they need to accept updates immediately? How often should they change their passwords? |
| Security Training | The purpose of this policy is to outline how you’ll educate your people to be better at data security. It’ll encompass what level of knowledge and behavior is expected and how they’ll be trained. It may include compulsory or optional options, including phishing training. |
| BYOD | This covers the rules and expectations relating to how your people can use their devices for corporate business: e.g., they must accept mobile application management and other data security protocols. |
| 3rd Party Access | This sets out what levels of access third parties like consultants or freelancers can have to your data and who’s responsible for granting access and monitoring them. |
Your Mobile Device Security Policy May Need A Tweak
OK, so we’ve made mobile device security policy sound gross and difficult. And downloading some random mobile security-ish policies from Policies’R’Us.com won’t cut it. Your policies are about your business and your people, and that means they need care when you’re creating and deploying them. We’ve had our heads up the butts of best practice security policies for over 23 years, so if you have a question, we’re here to help.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!

