In a world where smartphones, tablets, and laptops have become indispensable tools for modern workforces, the challenges of ensuring data security have reached new heights. The very devices that empower employees to work flexibly and efficiently also present significant risks to enterprise data. Striking the delicate balance between flexibility and security has become a paramount concern for organizations.
So, how can you achieve this equilibrium? The answer lies in the realm of mobile device management (MDM). By implementing an effective MDM strategy, you can harness the full potential of these devices while safeguarding sensitive information. A well-crafted MDM strategy enables you to assess, deploy, and maintain robust security configurations, empowering your workforce to remain highly productive while thwarting the nefarious intentions of hackers.
So, let’s unpack the critical importance of a mobile device management strategy in protecting enterprise data. We will delve into the key components that make up a successful MDM strategy and unveil the powerful benefits it brings to organizations.
What’s Mobile Device Management?
At its core, MDM empowers IT administrators to secure, control, and enforce security policies across various endpoints, including smartphones, tablets, computers, and more. However, MDM goes beyond being a mere software solution—it encompasses processes, policies, and human decision-making as well.
How Does MDM Work?
For MDM to operate effectively (or at all), your fleet of devices establishes communication with an MDM server. This server typically runs on a cloud platform and serves as the central hub for managing your devices.
The MDM Dashboard
To oversee your device fleet, your IT people access the MDM dashboard through the server. This dashboard allows them to remotely install software, track device inventory, and enforce configurations known as “policies.”
The MDM Application
Each device within your fleet has an MDM application, sometimes referred to as the “MDM agent.” This application acts as the mediator between the device and the MDM server. It receives commands from the server and implements them on the respective devices.
The MDM Toolbox
MDM is an ever-evolving landscape, offering a diverse array of optional services and tools tailored to meet enterprise needs. For instance, Ignition’s MDM solution provides an automated onboarding service, streamlining the setup process for users. Devices are shipped directly from the manufacturer to the user, who is then guided through the necessary steps to securely configure their devices. The MDM server pushes essential apps and enforces relevant security policies, ensuring a seamless and secure start to their work journey.
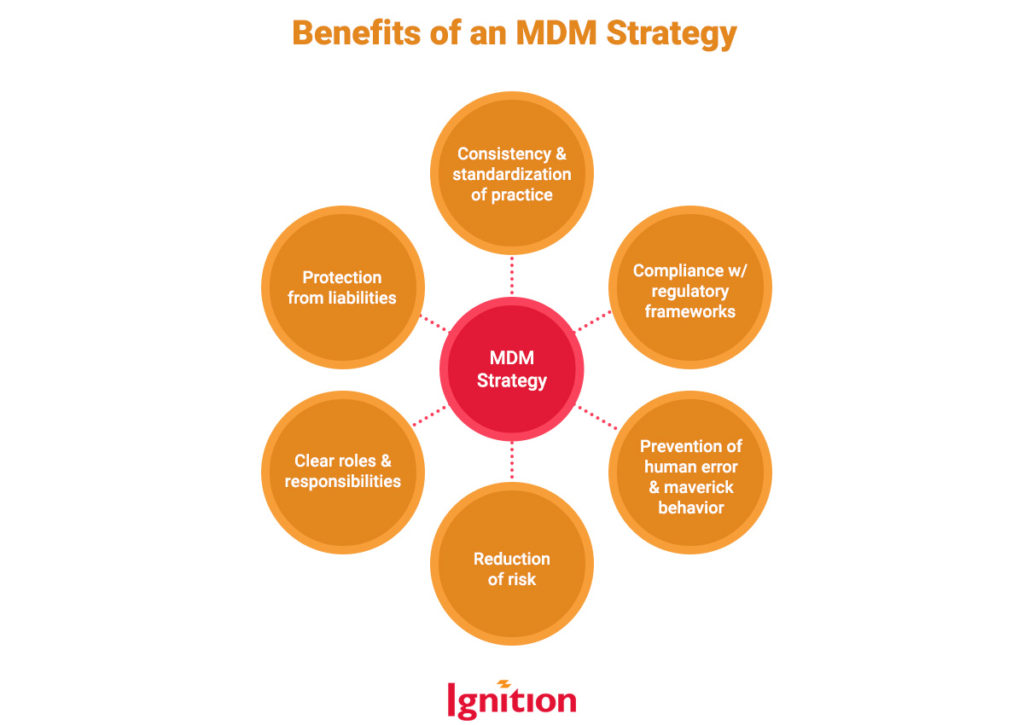
How Can a Robust MDM Strategy Protect Enterprise Data?
A good strategy makes everything better. Here’s how an MDM strategy strengthens data protection and business resilience:
What To Include In An MDM Strategy
To create a comprehensive MDM strategy that aligns with your business goals and IT strategy, consider including the following six elements:
1. Which Devices And People Are Included
Determine the composition of your device fleet. Will it be cross-platform, limited to Apple or Windows devices? Ensure that your MDM strategy aligns with your IT purchasing strategy. Additionally, decide whether to include devices belonging to freelancers, consultants, and permanent staff within your MDM fleet.
2. Acceptable Use Agreements
Define, document, and communicate the acceptable use of corporate devices. Establish an acceptable use policy that clearly outlines how corporate devices should be utilized. Additionally, consider implementing a Bring Your Own Device (BYOD) policy for personal devices in your fleet.
3. Enhanced Security Configurations
A comprehensive MDM strategy provides robust protection for enterprise data. Consider implementing the following security configurations:
- Access control configurations, including public Wi-Fi blocking, multi-factor authentication, and remote lock/wipe.
- App blocking and white/blacklisting to reduce the risk of inadvertently introducing ransomware and malware.
- Enforced operating system and software updates to ensure devices have the latest bug fixes.
- Automated data encryption to safeguard data during transmission against unauthorized access.
- Regular, automated backups to enable quick recovery in case of data loss.
- Location tracking and geofencing to retrieve lost or misplaced devices and monitor device boundaries.
4. Mobile Application Management
Mobile Application Management (MAM) is particularly useful for BYOD policies. It keeps corporate data separate and protected on personal devices, providing users with a secure “front door” for access. MAM may also involve application wrapping, which adds an extra layer of security without modifying the core functionality of enterprise apps.
5. Inventory Management
Leverage the inventory management capabilities of your MDM platform. It automatically collates and categorizes each device in your fleet, providing you with up-to-date IT asset inventory. Specify important aspects of inventory management in your MDM strategy, such as addressing red flags, routine checks for outdated OS versions or suspicious device behavior, and guidelines for device age thresholds.
6. Guidance on Integrations
MDM is not just about managing and securing your fleet; it can enhance your overall business operations. Determine which integrations will benefit your organization and define how they will be implemented. Some useful integration examples include:
- Automated onboarding and offboarding processes.
- Integration with cloud platforms and software.
- VPN integrations for secure remote access.
- Identity management integrations to streamline user authentication.
- Remote troubleshooting capabilities.
As organizations increasingly rely on mobile devices for productivity and flexibility, it becomes clear that implementing a robust MDM strategy is essential not only for protecting enterprise data but also for ensuring a seamless and secure mobile work environment.
Top Of Your To-Do List: A Robust MDM Strategy
MDM is so packed with business benefits that it can be difficult to extract the “must haves” from the “this would be kind of cools.” We’re here to help you detangle the world of MDM, so you can be clear on the best configuration for where your business is now and where you want it to be. MDM strategy is your starting point, so give us a call. We’re here to help.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!

