Geeks made out of real people.
Contact Us
Learn the basics of IT asset lifecycle management.
If the phrase “IT asset lifecycle management” doesn’t fill your heart with fairy dust and an unknowable gladness, then go back to the darkness from whence you emerged. But if you feel a pleasurable shudder at the phrase, you’ll know that you’ve arrived at a practice that’s fundamentally beneficial to all aspects of your business.
So, here’s our unasked-for-yet-hopefully-useful ultimate guide to the joy that is IT asset lifecycle management. You’ll learn:
But first, let’s go over some definitions.
We define an IT asset as company-owned information, hardware, or software that make up an IT ecosystem used for business purposes. You’re looking at:
Your happy family of IT assets takes care of a truckload of functions that keep your business doing its thing: Storage, control, display, data transmission, communications, and user management.
Now, it can get a bit sticky if you have a Bring Your Own Device (BYOD) policy, as your IT assets (company data and apps) are living on someone else’s IT asset (your employee’s personal device). But things like mobile application management and conditional access can solve that kind of problem.

Every IT asset has a shelf life. Just like us, it has a journey from womb to sustainable willow eco-casket. Simplified, the lifecycle of an IT asset starts when you take control of it. It continues as you use it, and then ends when it has outlived its usefulness to you and you dispose of it humanely. Sad face.
ITALM is a methodology of developing and administering IT assets in a way that gets the best out of them throughout their lifecycle. It’s a chunky subset of IT asset management (ITAM) and its purpose is to maximize benefits to your business and minimize pesky risks.
A note to digital asset fans: Prepare for sadness, because we’re not covering digital asset lifecycle management here. That’s because managing the lifecycle of digital assets is a bit too special. Yes, you’re looking at a similar process, but it’s complexified by specialist management tasks such as distribution, retrieval, and archiving.


Explain Like I’m Five: What Actually Happens in ITALM?
Sure. When you’re ITALM-ing like a boss, you’re:
ITALM is a business superpower that blesses you with the policies, tools, and strategies to make sure that your IT assets are used in the most effective way possible for your business objectives. Having a robust ITALM system in place contributes positively to:
Business Planning
ITALM gives you accurate, real-time visibility of all your IT assets. Your CTO will love this (and you) because this gives you the power to plan more effectively. For instance, if you need to hire, like, 25 people next May, do you have enough devices for them all? ITALM tells guesswork to go swivel because you’ll check your IT asset register (the Holy Baloney of ITALM) and it’ll tell you that you’ve four spares begging to be used, but you’re gonna need to order 21 more from Devices’R’Us. You’ll have those devices ready and waiting for your new people, like you know what you’re doing.
Cost Saving and Forecasting
With your IT assets visible, you’ll know when they’re gonna die. And this means you can plan the funeral and more accurately forecast when you’re going to need some dollars for the replacements. You can also schedule maintenance and upgrades more accurately, and this not only makes your assets last longer but you’ll look really good too. And, with a central source of truth for your IT assets, you’ll eliminate duplicate purchasing as well as the risks and costs of shadow or maverick IT purchasing, where devices and licenses are bought by employees or departments without the knowledge of the IT peeps. ITALM makes asset planning and purchasing more controlled, transparent, and safe.
Optimizing Usage
Because you can see how assets like software subscriptions or devices are actually used in real life, you can squeeze all the juicy goodness out of them, save costs, be more sustainable, or, double wowzer, all three. For example, with ITALM you’ll be able to:
Compliance
If you’re cornered behind a rundown gas station at a creepy rest stop at midnight by the ISO 27001 gang, just show them your ITALM colors and you’ll be fine. That’s because, if you’re doing ITALM right, you’ll have done all the heavy lifting towards compliance with a ton of regulatory frameworks, including the big momma herself, ISO 27001.
That’s because ITALM is a mechanism for your Information Security Management System (ISMS), which is the foundational component of most compliance frameworks. Elements of ITALM protect the holy trinity of compliance: Confidentiality, integrity, and availability.
Data confidentiality means that only authorized humans can get their mitts on your data. Data integrity means that only authorized humans can make changes to the data. Data availability means that the data must be accessible to authorized people when they need it. It’s just access control, people, with a side-order of making sure things don’t break.
With robust ITALM in place, you’ll be able to protect the data living in your assets (and keep data available for the right people) by:
So glad you asked. To be real, lifecycle stages can have different names, depending on who you ask/read/pay/pray to, but the principles are the same. Here’s our version:

1
Here’s where you bring new IT assets into your business, in line with your IT strategy and business goals. This could be as straightforward as buying a dozen corporate tablets or renewing a software license, or as complex as migrating your entire business to the cloud.
2
Got those shiny new assets? Time to prep them for use and release them into the wild. This could be as easy as zero-touch onboarding or as complicated as automating and testing a new quality monitoring system for your manufacturing plant that’s bigger than Idaho.
3
Use isn’t just any kind of use - nope, it’s authorized use, which is special. Here’s where that IT asset gets used to within an inch of its life, doing the job that it’s supposed to do.
Maintenance is bigger than a quick buffing of that laptop screen to remove the gross. It’s also about keeping that asset working, optimized, licensed, secured, and safe by monitoring and upgrading. And, don’t forget the dull but important things like safe storage, if the thing isn’t being used but it’s still in your inventory.
4
There’s a Gandalf and a Sauron of IT asset disposal. Controlled disposal (Gandalf) is planned and gracefully executed, e.g., your IT strategy says that tablets with more than six birthdays will be taken out and shot or offboarded securely to green waste. Uncontrolled disposal (Sauron) is a nasty surprise, e.g., Naomi’s corporate laptop containing all that customer data is stolen from Sizzler’s again. Whatcha gonna do? Hint: You have a policy for that and it’s called Lock & Wipe.
As an example of ITALM in action, let’s look at how mobile device lifecycle management works in real life. We’re picking on this type of endpoint management not just because we have a helpful diagram, hand-drawn in oils by our Ignition artist-in-residence, but also because this is what we do for a living, so we know what we’re talking about. Our version of mobile device lifecycle management is called Laptop Logistics and here it is.
Let’s take a look at each stage of the IT asset lifecycle management process and the associated best practices to get you started.
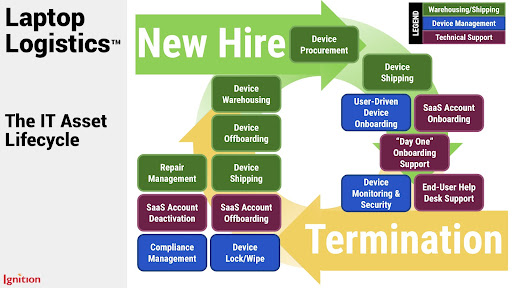

This is a biggie, as managing your IT asset lifecycles without actually knowing what assets you have and where they are is super difficult. For mobile endpoints like tablets and smartphones, your not-so-secret weapon is mobile device management. It’ll gather a detailed inventory of your current mobile devices, giving you visibility and central control over your fleet. This is the basis of your IT asset inventory and gives you the power to assign specific controls and policies to each device as well as monitor, track, and secure them.
Before you start buying a new kit, make sure that:


It’s time to get those devices ready to play.
With user-driven automated onboarding - such as zero-touch onboarding and cloud single sign-on - new hires get access to the apps, data, and platforms they need on hour one of day one. But that’s not the best practice. The magic is in the security processes of onboarding– shipping straight from storage or the manufacturer, reducing data risk. A secure sign-in process is also key to ensuring that only authorized newbies have access to corporate data and apps.
Sometimes a device lasts longer than the career of its user. That’s why spares management is a key ITALM best practice that keeps compliance managers especially ecstatic. The practice should include:


Decent ITALM keeps those devices secure, provisioned, and working while it’s doing its thing for your business.
Now that you have an IT asset registry (free with MDM!), use it to monitor your fleet. While your devices are in their in-use stage, it’s important to ensure they’re being used securely and appropriately. Your MDM dashboard will flag up potential security risks such as ancient OS or large file downloads.
When your IT asset has come to the end of its useful life, it’s time to say, “It’s not you, it’s me” and dispose of it securely and, hopefully, ethically.
Close those SaaS accounts. Wipe or transfer that data. Remote lock the device if you’re that worried. Courier it back to you or your trusted someone to dispose of properly. De-activate and remove mobile app management from BYOD devices.

All the cool kids are tackling ITALM because it’s a business asset that pays for itself a whole ton. Our IT asset lifecycle management services take care of your IT assets throughout, guess what, their lifecycle. If you’re thinking about giving ITALM a go, give us a call.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Call us now–chatting about IT support and cybersecurity is our favorite thing to do!

Get started!