Personal question barrage of the day: Do you transmit data about people’s health? Do you think you might be storing medical records somewhere in the cloud? Do you suspect you might be a covered entity? Are doctors, shrinks, and physios some of your best clients? If you answered “Yes” or made some kind of worried grunting noise, you probably need to know about HIPAA.
Dry those pits because we’re giving you a quick run-through of HIPAA’s cybersecurity requirements, followed by a special How To Get HIPAA-Compliant Checklist.
But First, HIPAA: A Quick And Dirty History
Once upon a time, back in 1996, when Los Del Rio’s “Macarena” was your earworm, god created the Health Insurance Portability and Accountability Act (HIPAA). This policy sought to reform the health insurance industry by increasing the portability of health insurance as people left one job to take up another.
Uh-oh. Increased portability allowed more people to transfer their individually identifiable health information electronically, which put the data at a huge risk of breach. Everybody has a right to expect their personal health information to stay, well, personal. That’s why, later on, protective cybersecurity standards were thrown into the HIPAA mix and became a requirement for anyone handling certain types of data categorized as electronic protected health information (ePHI). ePHI is protected health information that’s created, stored, transferred, or received in electronic form.
The end.
HIPAA’s Cyber Security Requirements
HIPAA is basically a set of themed rules, each of which outlines the different requirements for compliance:
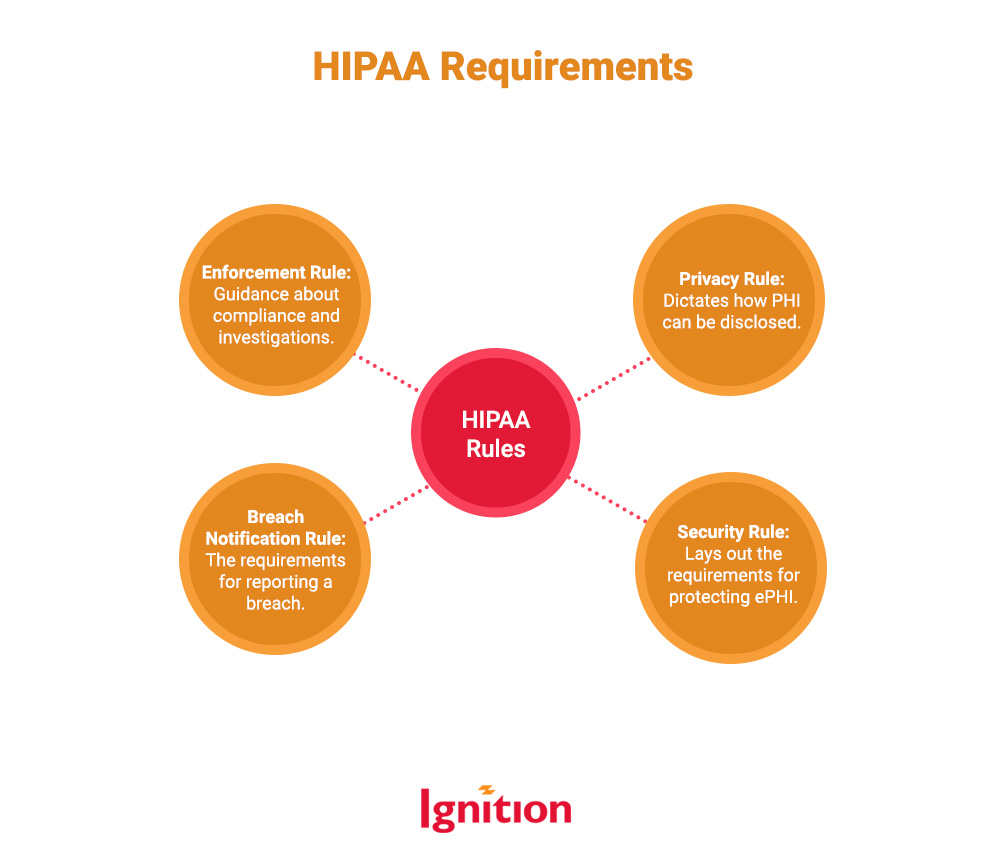
The Security Rule is the key rule for cyber security and lays out how you should safeguard ePHI. Safeguards are either “required” or “addressable,” which can get a little confusing. Required safeguards mean, yep, you’ve got to do them. Addressable safeguards provide an option to implement the HIPAA-recommended safeguard, adopt a different-but-just-as-effective protective measure, or not adopt it if there’s a justifiable rationale.
HIPAA’s Security Rule
The Security Rule tells covered entities and their business associates (i.e., organizations that deal with health data, although there are exceptions) that they have to maintain a range of administrative, technical, and physical safeguards to protect ePHI. Here’s what they look like:
Security Rule Safeguards
| Type of Safeguard | Examples of safeguard controls |
| Administrative |
|
| Technical |
|
| Physical |
|
You may already have a truckload of those safeguards down as part of your normal grown-up handling of data. But how can you be sure? This is where you turn to your Super-Duper How To Get HIPAA-Compliant Checklist.
Super-Duper How To Get HIPAA-Compliant Checklist
Start here:
1. Complete a Readiness Assessment and Gap Analysis
Your first hop, skip, and jump on the HIPAA adventure should be getting all up in a HIPAA readiness assessment. This is a security audit that focuses on what HIPAA wants. It’ll tell you both the good and bad news:
Good = Hey, here are the bits of HIPAA that you’re already doing. Go you!
Bad = Uh-oh, you suck at this part of HIPAA, so let’s stick the bad stuff in your Big List Of HIPAA Gaps To Fix.
HIPAA is a specialist framework, so we advise you to pick a decent HIPAA risk/readiness assessor to do the job for you. Employing a third-party partner with the necessary smarts and qualifications will stop you from overlooking or misinterpreting HIPAA regulations. Here’s what you should get at the end of it:
- Where and how your current cybersecurity controls comply with HIPAA’s security requirements.
- A list of gaps: where your current arrangement falls short of HIPAA.
- A prioritized list of recommendations to get you up to HIPAA compliance standards.
2. Create a Remediation Plan
The prioritized list created by your assessor will help you build a roadmap to compliance: you’ll know which are the biggies you need to address first and the steps to resolve them. Your remediation plan should cover:
- Prioritization of gaps.
- Remediation action: What steps need to be taken to fix each gap.
- A timeline for the remediation activity and milestones to track progress.
- Roles and responsibilities: Who’ll do what and who has overall control and accountability for the remediation project.
- Communication: What and how you’ll communicate with stakeholders, including team workers, suppliers, the covered entity (if you’re a business associate), or the individuals whose health information you’re using.
3. Update Your Data Security Policy and Strategy
Change management starts with policy. HIPAA compliance should become part of your overall IT strategy framework and data security policy for your business. Your policy is saying, “We need to be HIPAA compliant, and therefore we’ll consider all the HIPAA security requirements in each decision we make.” Once you’ve imbued your data security policy with HIPAA loveliness, it’s time for Step 4.
4. All The Implementation
Here’s where you take action to close all those gaps, be they administrative, technical, or physical. Use your favorite project management techniques and get going! Hint: We’re gap remediators par extraordinaire (that’s French for “ever so good”), so hit us up for this bit. And for the planning stage.
5. Did It Work? And Does It Still Work?
Test, review. Test, review. Ad nauseam. You know the drill. Test as you implement, and then check everything out at the end of the implementation step. Are you compliant now? Bring your favorite HIPAA assessor in to check. And keep monitoring.
HIPAA Cybersecurity Requirements Shouldn’t Make You Weep Angry Tears
If you deal with ePHI, HIPAA is not optional. Look on the bright side. It may seem daunting, but it’s not half as scary as ISO 27001. HIPAA’s cybersecurity requirements are pretty standard, really – there’s nothing that’s not doable. The challenge is to recognize where you’re going wrong (one for your HIPAA assessor) and then put it right (ahem, our MDM services alone will give you about a quarter of HIPAA requirements. Just sayin’.) Why not start with an informal non-salesy HIPAA-flavored chat with one of our friendly experts? Go on, we dare you.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!
