“I prefer device onboarding for a remote workforce that’s as difficult as possible,” said nobody ever. Device onboarding for a remote workforce doesn’t have to be an uphill battle. So, let’s explore a solid approach and useful protocols to ensure a smooth and secure onboarding process. Whether you’re welcoming new hires or transitioning to a fully remote setup with existing staff, these strategies will help you achieve efficient onboarding without compromising on security.
Device Onboarding: What You’re Aiming For
The ultimate goal of device onboarding is to avoid common pitfalls that can hinder productivity and pose security risks. To ensure a successful onboarding process, aim to prevent the following:
- Mis-provisioned devices and lengthy setup times leading to decreased productivity and performance.
- Overburdening your IT team with a barrage of user problems or requests during onboarding.
- Increased vulnerability gaps and unauthorized access caused by security misconfigurations and non-compliant devices.
- First-day mishaps for new hires resulting in lower retention rates and higher recruitment costs.
You want a streamlined, clear onboarding process that gets your people up and running quickly while keeping devices secure. So, what’s the recipe for best practice device onboarding for your remote workforce? Let’s take a look.
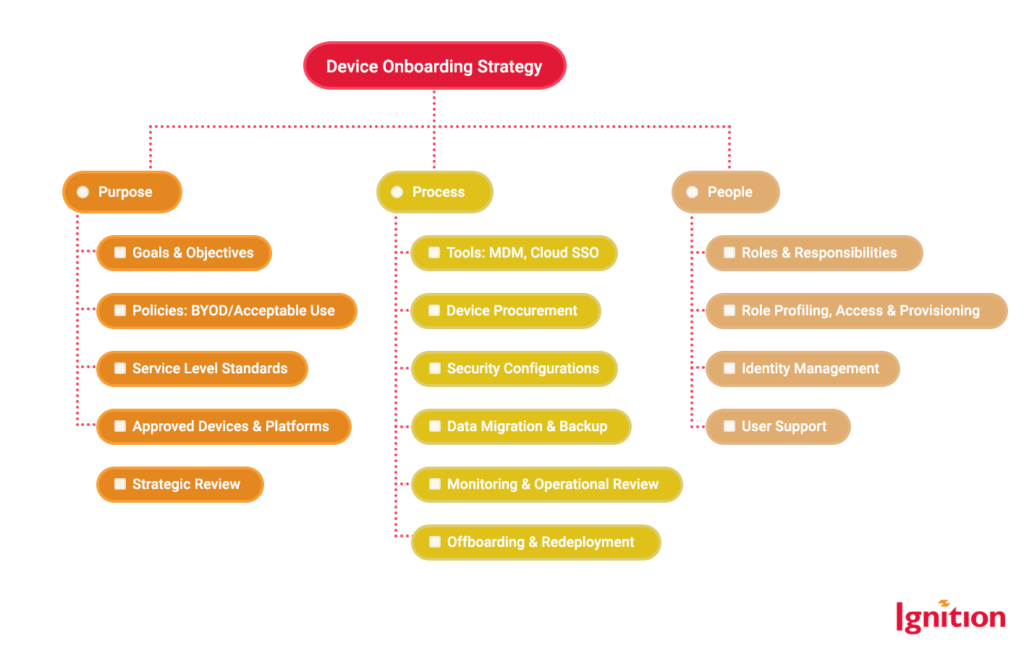
1. Create A Device Onboarding Strategy
The foundation of a successful device onboarding process lies in having a well-defined strategy. Your device onboarding strategy should be adaptable to the changing needs of your business and cover crucial issues such as:
- Optimal deployment of device onboarding.
- Ensuring flexibility and scalability as your business evolves.
2. Create An Onboarding Checklist
Your onboarding checklist is the operational guidance that keeps you on track to onboard your workforce (whether new hires or existing employees) smoothly and efficiently. A robust onboarding checklist is a virtual, editable document shared with relevant staff that details the onboarding process and tracks progress.
It’s not rocket science, as it’s just a list that details:
- Clear tasks and actions required during onboarding.
- Timelines for each task.
- Designation of responsibilities among team members.
- Progress tracking to ensure nothing falls through the cracks.
It’s incredible how useful a good onboarding checklist is, and it outlives your IT staff as they come and go. It also solidifies the onboarding process because, as you create it, you’ll come up against issues to resolve that you can fix ahead of time rather than wait until you’re in the middle of onboarding to find out that something doesn’t work.
3. Use the Right Tools
Using the right tools is the difference between seamless, fast onboarding and a nervous breakdown. Your strongest tool to deploy devices to a remote workforce is mobile device management (MDM). MDM gives you centralized control over a fleet of devices which includes the ability to:
- Enroll devices, whether new or existing.
- Provision devices with necessary apps and access for individual users.
- Implement security configurations for endpoint defense, such as antivirus, antimalware software, and encrypted file sharing.
With MDM, you can onboard a current workforce with existing or new devices and new hires with new devices. Onboarding with new devices is particularly exciting because MDM blesses you with the benefits of zero-touch or conditional onboarding.
Zero-Touch Onboarding
With zero-touch onboarding, you’ll never have to see or touch that new device. That’s because your new hire will do all the touching, in terms of unboxing and booting up said device, Fedexed to them straight from your device supplier. They’ll be guided to complete the setup, which takes twenty minutes.
Conditional Access Onboarding
If you have a Bring Your Own Device (BYOD) policy, conditional access onboarding ensures that privately-owned devices adhere to your corporate security policies before allowing access to corporate data. This means you can deploy security protections such as enforced passcodes, OS updates, and encryption so that privately-owned devices don’t become a vulnerability.
4. Don’t Forget Offboarding
The offboarding process is often overlooked but is equally essential. Properly managing offboarded devices is critical to minimizing security risks.
Issues to avoid during offboarding include:
- Leaving user accounts open and vulnerable.
- Losing track of offboarded devices’ physical location.
- Paying for unused software licenses.
- Allowing ex-hires to retain access to sensitive information.
MDM’s asset register will tell you exactly where your offboarded device is, and from your MDM dashboard, you’ll be able to secure the device and reprovision it for the next user. In a worst-case scenario, you can lock or wipe that device.
How To Onboard Devices For Your Remote Workforce: Step One
The first step is to give us a call. Whether your business is fully remote, or hybrid, you’re looking to scale up quickly with an expanded workforce, or you need to hire a team abroad, we can provide expert advice on device onboarding tailored to your specific needs. Our team is here to help with your current and future device onboarding requirements.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!
