Unlike BYOB, Bring Your Own Device (BYOD) is no fun at parties, but that shouldn’t stop you from considering it as A Thing You Should Do, especially if you’re a small business. When done right, BYOD is stuffed full of business advantages. Dear reader, cast your peepers down at our favorite BYOD best practices for small businesses.
Hang On, Why Is BYOD Good For Small Business, Anyhow?
So glad you asked. Many SMEs leap fully clothed into the world of BYOD because of its cost and productivity advantages. Look at this pretty diagram:
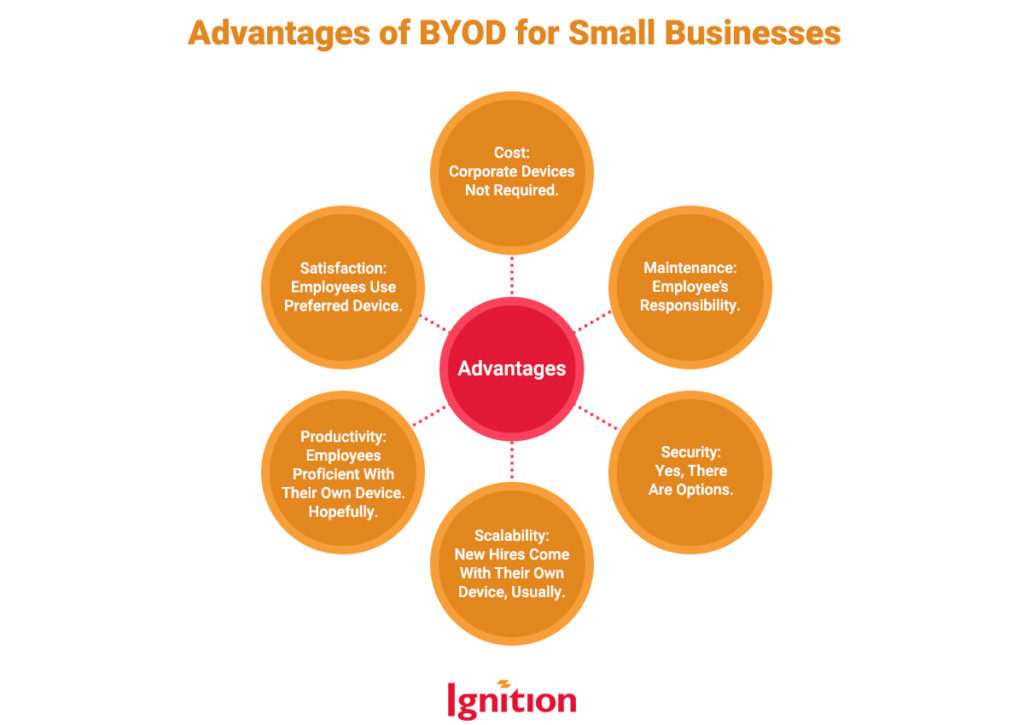
For BYOD to work, it needs careful handling. The key challenges are:
- Control: You don’t have the same governance over personal devices as you would over corporate devices. You need a different approach.
- Security: For starters, personal devices can be used by employee families, neighbors, church groups, etc. Software may not be updated. Devices may connect willy-nilly to unsecured wifi. It can get dark.
- Private vs. corporate data: There are complexities in how these are separated and treated.
- Support and maintenance: How can you ensure a private device is maintained to a high corporate standard?
- Exit: How do you secure corporate data when your people leave/are fired?
Don’t let this list of sadness put you off: with a shot of best practice, you can go to the BYOD ball too.
Three BYOD Best Practices for Small Business
Let’s get into it. First off, everything starts with policy.
1. Create A BYOD Policy
You already know that good policies make everything better. A good BYOD policy gives you an agreed benchmark, set of standards, and guidelines on how BYOD works in your organization. So, what’s in a BYOD policy? Everybody’s different, but here are the critical policy areas you need:
| BYOD Policy Guidelines | |
| Acceptable conduct/use | Clarifies what’s permitted and what’s prohibited: guidance on data sharing, appropriate content, what’s unauthorized access, requirements for handling data, accepting security processes, and prohibition of illegal activity. |
| Authorized devices and networks | Defines what devices are eligible, what networks and VPNs are allowed, and the minimum standards of software and hardware required. |
| Agreement about device control | Clarifies how personal devices might be controlled by the organization, e.g., through MDM and MAM. |
| Security measures | Clarifies security standards and the configuration required pre-enrollment as well as the use of passcodes; accepting security updates and antivirus software; incident reporting. |
| Data policies | Defines ownership of data; data retention; privacy issues; separation of corporate and private data. |
| Exit procedure | Defines how corporate data is secured and extracted from private devices as part of your offboarding checklist and who’s responsible. |
| Employee agreement | Employees are to read, understand, agree, and acknowledge the BYOD policy as part of the terms & conditions of employment. |
Once you’ve got your policy down, it’s time to enroll and secure those bad boys.
2. Use MDM
MDM is how you get those personal devices enrolled, in control, and in compliance with your corporate security standards. First off, onboard your people’s devices using conditional access, an onboarding methodology that ensures the devices adhere to your security standards before they are let into the party. Conditional access can require a whole truckload of security standards, like:
- Multi-factor authentication
- Ensuring the device has up-to-date software and licenses, and, if not, pushing relevant updates
- Session controls, e.g., timeouts or idle session sign-outs
- Location-based controls, e.g., if a device ends up on vacation in Mexico, access to corporate stuff is blocked automatically
3. Use Mobile Application Management
Mobile application management (MAM) is a subset of MDM. It’s a cheeky little invention that gives you centralized control over the corporate apps and associated data that’s sitting on all those private devices. It allows you to:
- Create a repository of corporate or store-bought apps which your employees can access
- Push, block, or allow apps
- Keep corporate and personal apps and data separate on each device by throwing all the corporate stuff into a protective virtual container
BYOD Is Pretty Useful, So Give It a Shot
BYOD shouldn’t throw you into a loss-of-control maelstrom any more than usual. These three BYOD best practices – a sound BYOD policy with sides of MDM and MAM – will create order out of chaos and give you the confidence to set your people free to use the devices they know and love. We’ll help you take that first step.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!

