So, you’ve loaded up your remote team with all the devices they could ever want and corralled them all into a sleek productivity machine with the help of a dose of shiny mobile device management. Go, you! But now you’ve got the tools to monitor the heck out of that fleet of devices, so where do you actually start?
With the right tools, monitoring your remote workforce becomes essential for maintaining efficiency and ensuring smooth operations. To get you up and running, let’s look at five essential IT monitoring best practices that will empower you to keep a watchful eye on your remote team. By implementing these practices, you’ll not only boost productivity but also enhance security, proactively troubleshoot issues, and foster a seamless remote working environment.
Remind Me, Why Do We Need To Monitor Stuff?
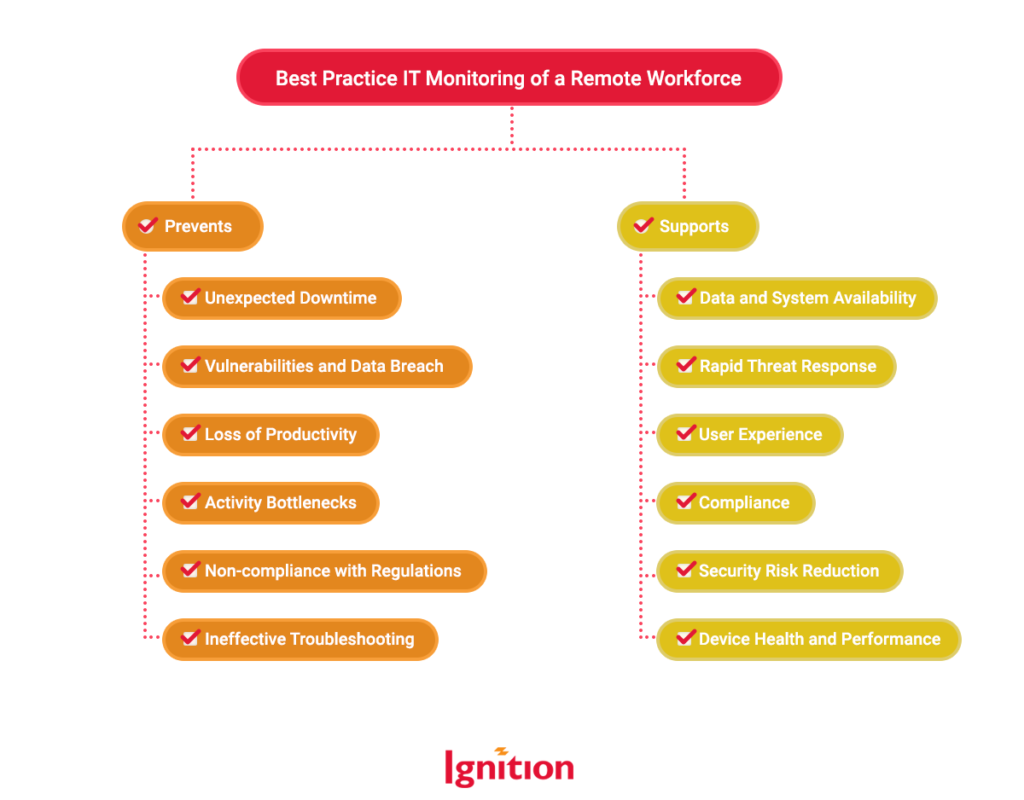
The big purpose of IT monitoring is twofold: it aims to prevent undesirable events and promote the occurrence of positive outcomes. But why is monitoring so crucial for your remote workforce? Let’s take a moment to refresh our memory and explore the reasons behind this essential practice.
Best practice IT monitoring encompasses a range of activities that support your business, including data and system security, system reliability, and productivity. By implementing a comprehensive IT monitoring system, you can reap numerous benefits that contribute to the overall success of your remote operations. Here are some of our favorite benefits we’d like to highlight:
Our Five Favorite IT Monitoring Best Practices
When it comes to IT monitoring best practices, it’s easy to get lost in the granular details. To get you started on the right track, we’re going to focus on the big picture. Here are our top five IT monitoring best practices that will set you up for success:
1. Have an IT Monitoring Policy
Everything begins with a policy. Your IT monitoring policy articulates the who, what, where, why, how, and when of IT monitoring within your organization. It should align closely with your IT strategy and clearly define objectives, roles and responsibilities, timescales and procedures, security and productivity configurations, metrics, and performance criteria. Additionally, consider any special areas of your business that require heightened IT monitoring, such as a remote workforce, compliance accreditations like SOC 2, special security requirements in sectors like healthcare or defense, or if you have experienced a previous breach that you cannot afford to repeat.
2. Ensure IT Monitoring Coverage is Comprehensive
IT monitoring is not a candy box where you can pick and choose your favorites while ignoring the nuts. Best practice dictates that you cover all areas. Here’s an overview of what to include in your IT monitoring process:
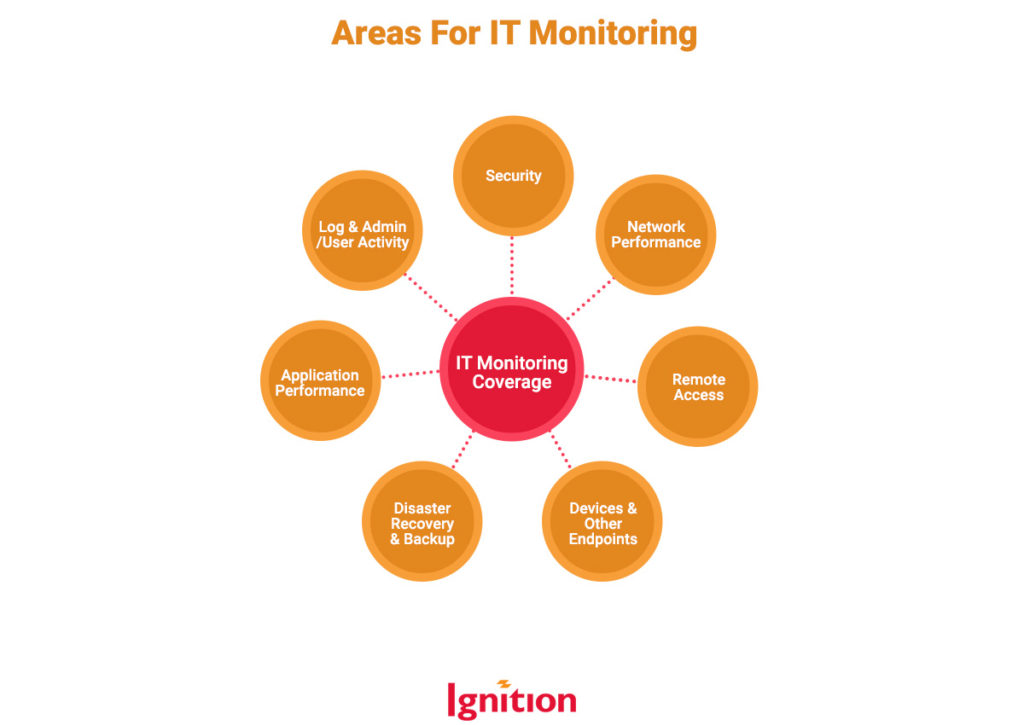
For bonus points, you might also want to monitor your people’s experience as users.
3. Have The Right Tools and Configurations
For a remote workforce, your top-of-the-list monitoring tool is, of course, Mobile Device Management (MDM). It’s a powerhouse of endpoint multi-monitoring that’s crystallized into the joy of a single dashboard. MDM enables real-time IT asset registration, ensuring compliance and enabling the detection of various nasties, such as:
- Outdated operating systems and software
- Unencrypted devices
- Anomalies like memory-intensive file downloads
- Devices moving outside expected locations
- Insecure or unauthorized Wi-Fi connections
- Malicious or unauthorized apps
- Phishing attempts
- Jailbroken or rooted devices
Additionally, as cloud computing plays a significant role for remote teams, consider selecting reliable cloud monitoring tools to assess the health of your cloud infrastructure. Choose a platform-focused tool like Azure Monitor for Microsoft Azure or a multi-platform monitoring service like Datadog, depending on your setup.
4. Automate, Automate, Automate
Automation is key. By incorporating automation and self-healing capabilities into your monitoring space, you not only save time and reduce manual effort but also enhance the effectiveness, efficiency, and proactive nature of your IT monitoring. Automation benefits include:
- Enabling rapid threat response by detecting, flagging, and dealing with security threats in real time.
- Enhancing security through 24/7 monitoring.
- Identifying performance bottlenecks to save costs and improve worker time.
- Improving IT management insight by collating usage, performance, and security data.
5. Review and Optimize
IT monitoring should never be a “set-it-and-forget-it” activity. It’s a dynamic process that should be regularly reviewed, honed, and optimized to align with your changing business needs.
Consider the following steps:
- Reassess your monitoring objectives: If your business has evolved, make sure you continue monitoring the right aspects with the appropriate depth. Are there new areas to cover or compliance regulations to adhere to? Look to other organizations in your industry for insights. Stay aware of emerging threats that your monitoring may need to address.
- Review serious incidents or near-misses: Analyze what went wrong and evaluate how well your IT monitoring infrastructure coped. Identify areas that require improvement or adjustment.
- Review your metrics and performance indicators: Ensure that your metrics are still relevant and provide valuable insights. Identify any additional data points you need to measure and collect.
- Audit your IT ecosystem to identify monitoring gaps: Sometimes, potential security or performance gaps may not be immediately apparent until a serious incident occurs. Regularly review datasets gathered by your IT monitoring processes to spot anomalies and address any gaps in monitoring coverage.
By following these five best practices and maintaining a proactive approach to IT monitoring, you’ll be well-equipped to ensure the stability, security, and success of your remote workforce. Sound good? We think so.
IT Monitoring Doesn’t Have to Be Painful
Here’s the thing. IT monitoring, especially for a remote workforce, can be a lot of fun because, if you build the right setup, most of it is done for you. That means you can get on with more strategic and fun stuff but still have a super-effective means to keep your data, devices, and people safe. If you’d like to take some solid steps to deploy these IT monitoring best practices for your remote workforce, give us a call. We’re here to help.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do! Don’t take it from us, our customer satisfaction is through the roof!

