We don’t mean to get personal, but wow, would you just look at the size of the attack surface on your business?? How did it get so big? Is it because your people are fully remote now? Have you got a gazillion free-range mobile devices flitting about the country, unmanaged and unmanageable?
You’ve heard of Mobile Device Management (MDM), right? It’s not just a “nice-to-have” option for your IT environment anymore – it’s a fundamental requirement for any secure IT infrastructure. So let’s get you started with our guide to implementing mobile device management.
Wait Up, Remind Me What MDM Is, Please?
Of course. MDM is a mashup of tech, people, and policies that, together, create a secure environment for people to work remotely. MDM gives you central control over all your devices and allows you (or your friendly neighborhood MDM service provider…ahem, us) to configure them securely, via remote commands and corporate and/or user profiles.
MDM is used to:
- Monitor devices to maintain compliance with different regulations and security policies.
- Update software and device settings.
- Remotely lock devices and/or wipe the data.
- Track device locations.
- Control access to apps and websites.
- Create and maintain an IT asset inventory.
If you think it sounds awesome, you’d be correct. So, how do you go about implementing MDM? Let’s take a look:
1. Get Yourself An Implementation Roadmap
You can’t get out of having an MDM implementation strategy. Here’s what should be on it:
- Research 1: Know what you have.
- Research 2: Know what you want.
- Policy: Here’s how you’ll do it.
- Who to call for help and how to do that.
2. Know What You Have
Here’s where you map out all the devices, or endpoints, that are used for your business. An endpoint is essentially an entry or exit point to your IT infrastructure. Endpoint devices can include:
- Laptops
- Smartphones
- Tablets
- Servers
Endpoints can also be virtual, like Virtual Machines (VM) that run in the cloud, but MDM is primarily designed to control mobile devices (hence the name, duh). Don’t forget to consider the devices your company does not own and manage, such as personal devices used for business or those used by freelancers and consultants.
Another issue to consider is the platforms from which your people work. If you’ve got a mix’n’match collection of Windows, OS, iOS, and Android, you’ll need a cross-platform MDM solution.
Now that you know the scope of what you’re trying to protect, it’s time to think about how you’d like to protect them. What would you actually like MDM to do?
3. Identify Your MDM Security Goals
Don’t know where to start? Ask yourself how your people use their devices. From this point, you’ll start to understand more about which aspects of MDM will meet your requirements. Try this on for size:
| Personality Quiz: Your IT Ecosystem | |
| Company Quirks | MDM Solution |
| Your people are on the road. | Remote lock/wipe; insecure network blocking. |
| Your people forget their passwords or create easy-to-break ones. | Multi-factor authentication (MFA); enforced passcodes. |
| You have a Bring Your Own Device policy. Or you need one. | Mobile Application Management (MAM). |
| You recruit remotely | Automated onboarding: zero-touch (corporate devices) or conditional access (BYOD devices). |
| You have no policy for closing user accounts after you’ve fired people. | Offboarding control. |
| Your software might be outdated. You don’t actually know. | Automated OS and software monitoring and updates. |
| You or your people have been phished. | App blocking; denylisting; monitoring; antivirus software; anti-ransomware configuration. |
| The whole company has access to corporate data and files. | Role-based access; file and data encryption. |
| There have been attempts to jailbreak devices. Ouch. | Monitoring. |
Once you’ve established your security vulnerabilities, you’ll have a wishlist of MDM services. Go, you! Next, it’s time to:
4. Establish Clear Policies
Good policies make everything better. For MDM implementation best practices, you’ll need a truckload, but don’t panic because all a policy does is clarify an accepted way of doing things across different themes. Here are the key policies you’ll need:
Implementing MDM: Key Policies
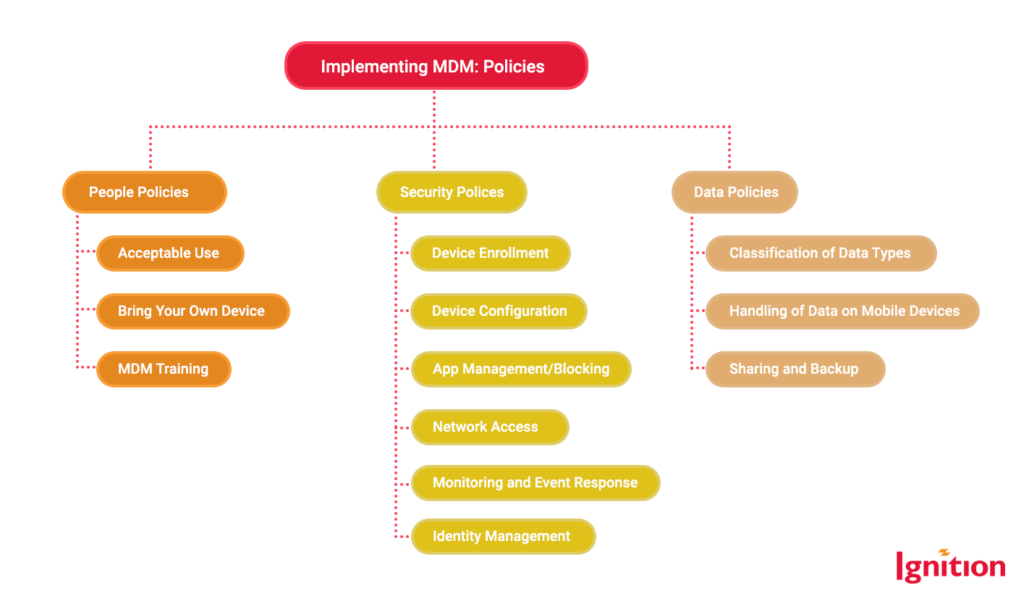
Note: Please change bubble in middle column to read “Device Enrollment” (two “l”s)
People Policies
If your people are using corporate-owned devices for work, you’ll need an Acceptable Use policy, which should be part of your employees’ contracts. Data security isn’t your sole responsibility as a business owner. Everyone in the business has a duty to protect data reliably, and that includes how people use mobile corporate devices. Part of your Acceptable Use policy should outline your team’s responsibilities for keeping data safe, including:
- Good password practices, like never sharing passwords, creating strong passwords, and/or accepting identity management protocols.
- Updating software and OS when asked.
- Keeping corporate devices physically secure.
- Using only approved apps and websites.
If you’re offering BYOD, a BYOD policy requires your team’s personal devices to be compliant with company security policies, addresses privacy and the separation of personal and corporate data, and defines how corporate use is managed (usually through the beauty of mobile application management).
Security Policies
These vital MDM policies detail the requirements and configurations necessary for keeping your fleet of devices to a high standard of security. These can be super-technical, but they’ll also cover roles, responsibilities, and processes: for example, if MDM detects a problem, what’s the resolution process, and who’s responsible for it?
Data Policies
Your people and security policies all have the protection of data at the heart of them, but what data are you talking about? Your data policies clarify how you categorize and treat data. It pays to know about the different kinds of data in your system and the levels of security it’ll need. For instance:
- Personal data like health information or data related to children has federal and state protection through HIPAA and FERPA, respectively.
- State laws like CCPA and the New York SHIELD Act protect data in those locations.
- Your own corporate data and intellectual property have value for cybercriminals.
- Compliance regimes such as SOC 2 stress the requirement for protecting the privacy, confidentiality, and integrity of data.
5. Implementing MDM: Here’s Where You Call For Help
Phew! You’ve done a ton of work, and we’re exhausted just reading about it. Well done, you! If you’re feeling overwhelmed about implementing MDM, this is where we come in to soothe your fevered brow. Puzzled about any aspect of MDM? Want to start enrolling those devices into a super-secure, standardized, and optimized fleet? Ready to slim down those chonky attack vectors? Call us; we can help. Why not start with a quick chat with one of our friendly experts? We triple-dog-dare you.
Ignition is Silicon Valley’s best (and friendliest) IT security, compliance, and support team. Contact us now – chatting about IT support and cybersecurity is our favorite thing to do!

